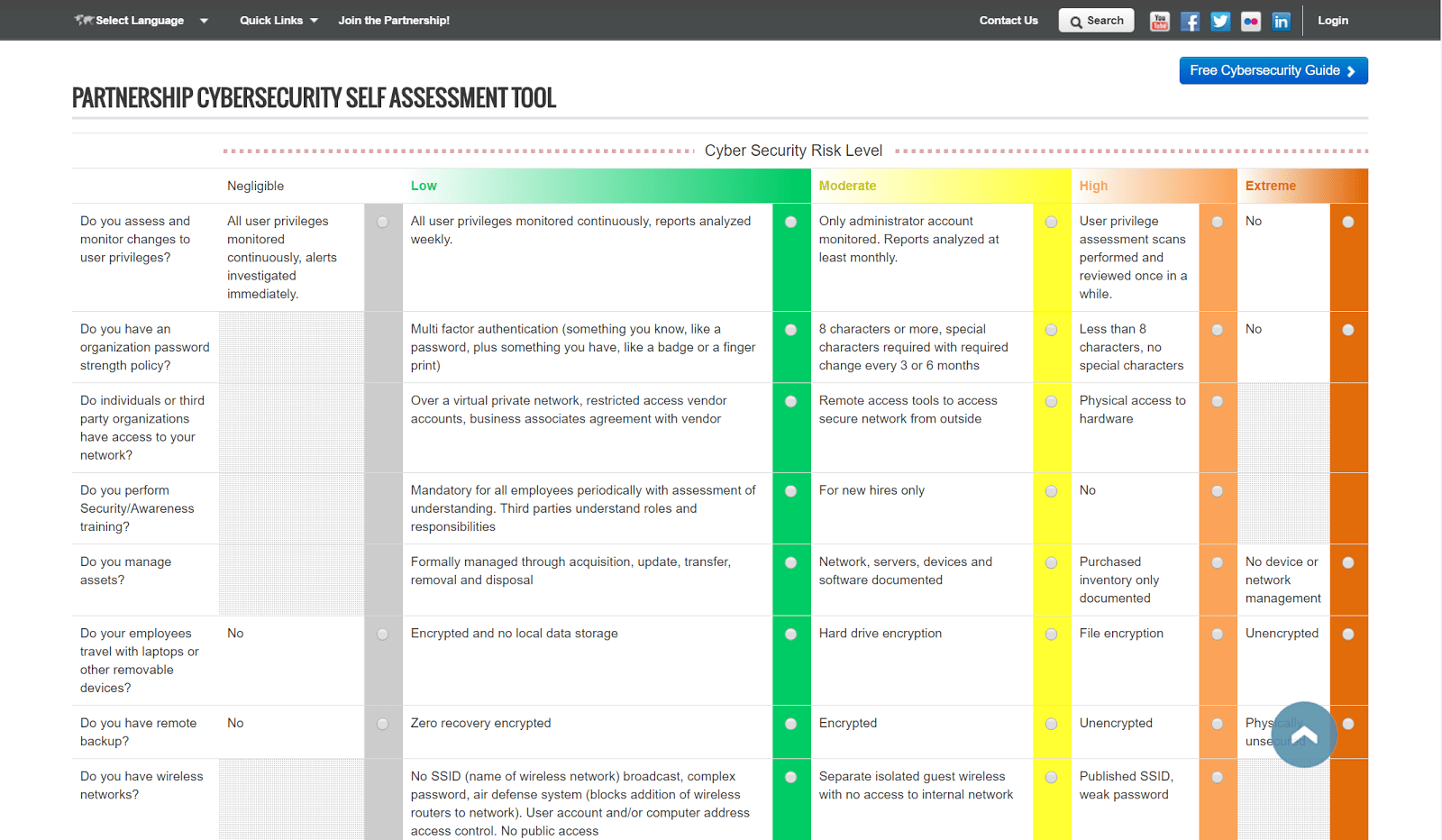
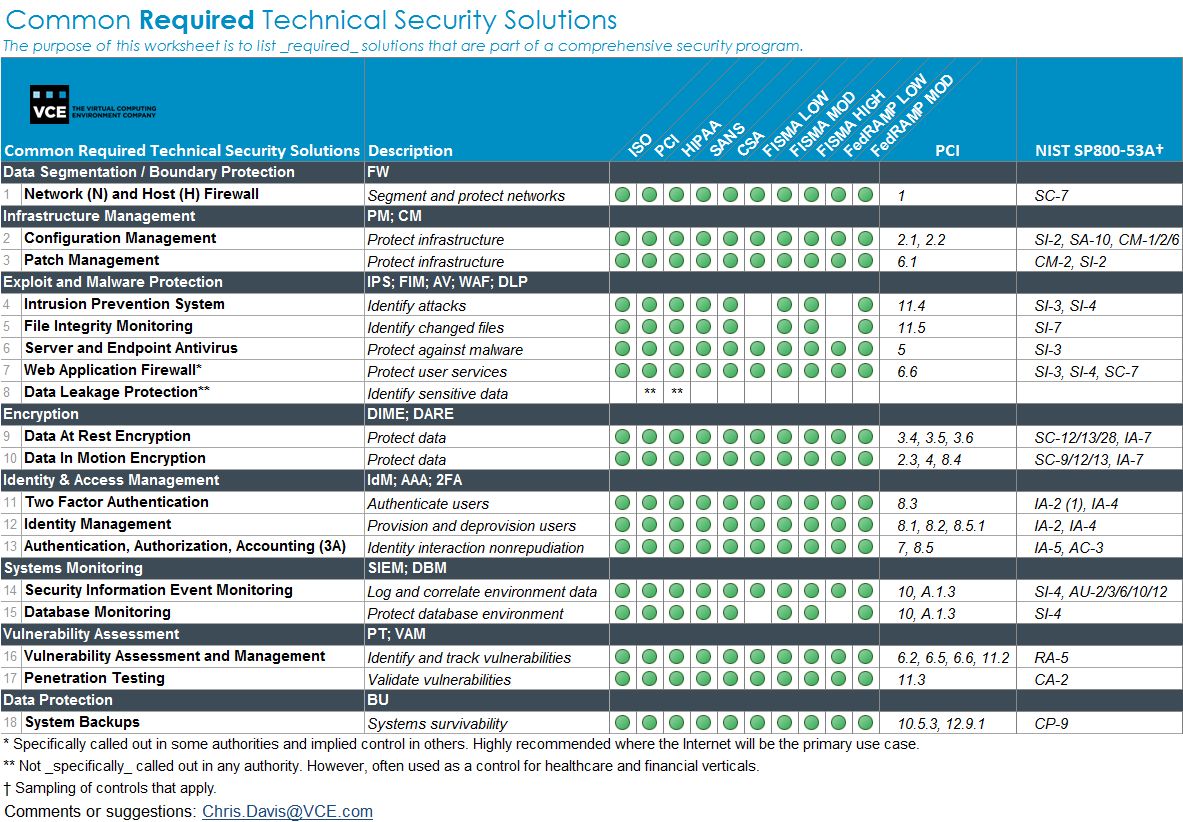
Cyber Security Audit Template

When implementing successful cyber security there is a whole plethora of things to consider.
Cyber security audit template. Keep your operating systems updated. The objective of a cyber security audit is to provide management with an assessment of an organizations cyber security policies and procedures and their operating effectiveness. Based on the nist cybersecurity framework an audit program based on the nist cybersecurity framework and covers sub processes such as asset management awareness training data security resource planning recover planning and communications. The development of a cybersecurity audit checklist should not only take into account the various software platforms that your employees use as part of their day to day responsibilities but also the online tools that they use from time to time to boost their productivity.
If you are a small medium size business you should ideally cover the following headers. Service agreements cloud services data security controls corporate insurance coverage. Cybersecurity assessment cybersecurity audit. The risk of free online tools.
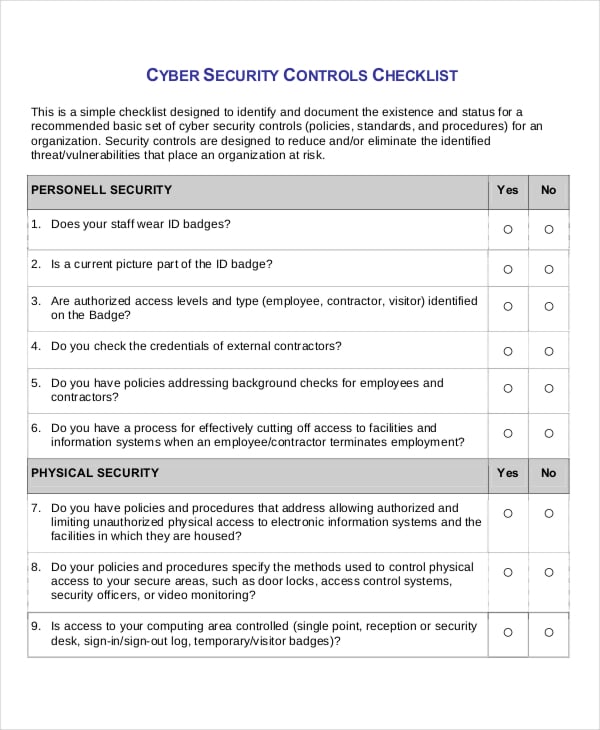
The audit program is based on the nist cybersecurity framework and covers sub processes such as asset management awareness. Information systems audit and control associations implementing the nist cybersecurity framework and supplementary toolkit isacas cybersecurity. For cybersecurity audit i suggest you follow a three column process. Cyber security controls checklist this is a simple checklist designed to identify and document the existence and status for a recommended basic set of cyber security controls policies standards and procedures for an organization.
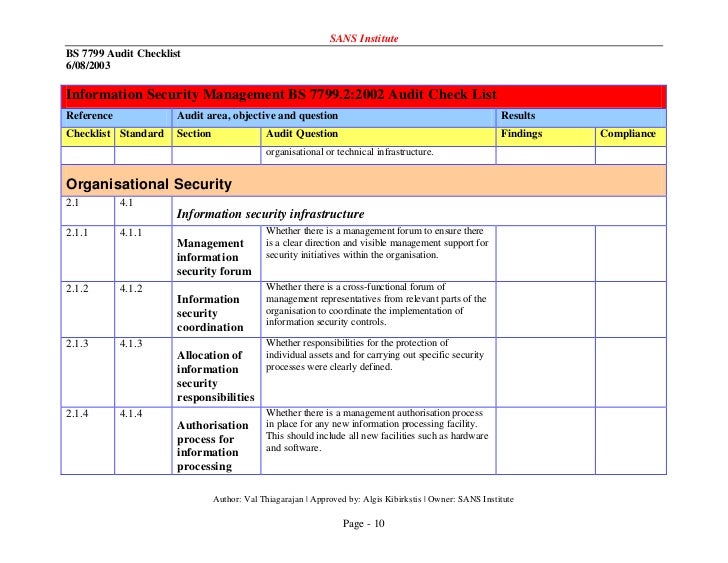
Audit area current risk status and planned actionimprovement. We created a list of relevant steps that you may want to incorporate into your own checklist in order to make sure that your company has all the necessary precautions in place. Moreover you can put these best practices into actionbe sure to check out our audit program template for cyber security. Existence accessibility of information security policy.
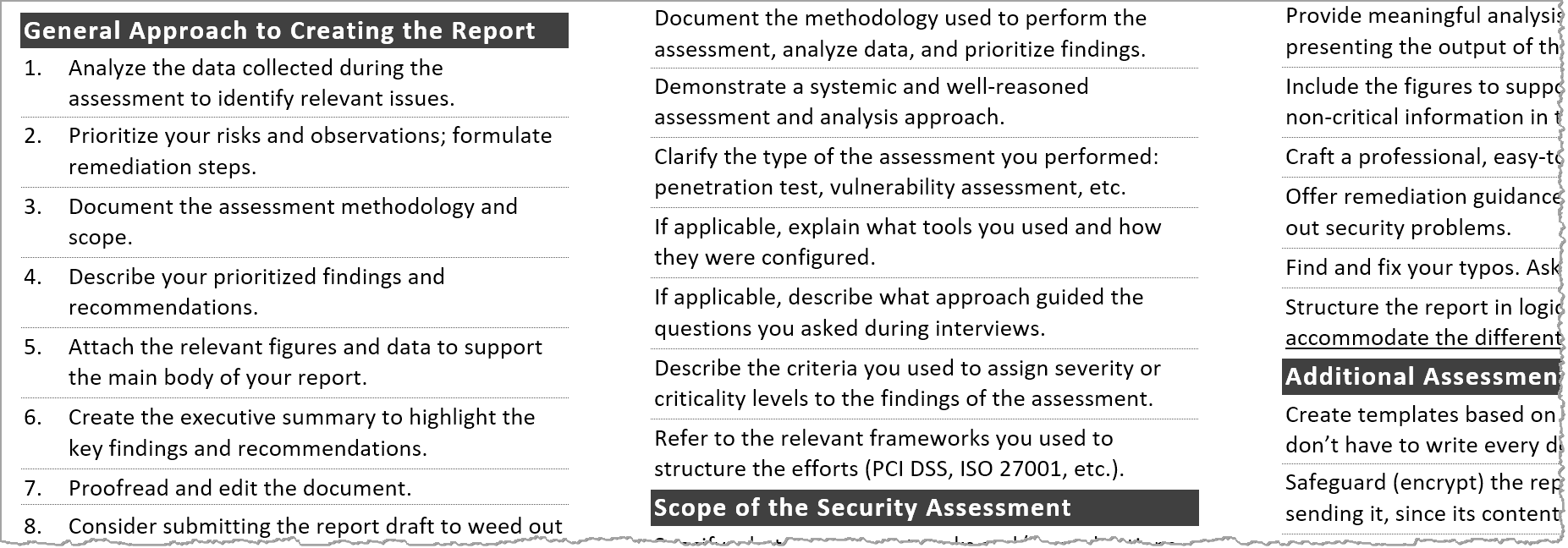
Formulating your cyber security checklist. Based on the nist cybersecurity framework is an is auditassurance program that provides management with an assessment of the effectiveness of cybersecurity processes and activities. Here is the top 20 cyber security audit checklist borrowed from aicpa designed for professional firms and small businesses who want to protect themselves from all known cyber threats. The purpose of a cybersecurity audit is to act as a checklist that validate that what youve said in a policy is actually happening and that theres a control mechanism in place to enforce it.
Your organization has a number of cybersecurity policies in place. Identify protect detect respond and recover. Password management data categorization segregation access storage and retention process suppliers cybersecurity practices. Additionally cyber security audits identify internal control and regulatory deficiencies that could put the organization at risk.