Cyber Security Implementation Plan Template
Set your cybersecurity priorities and draft a plan of action.
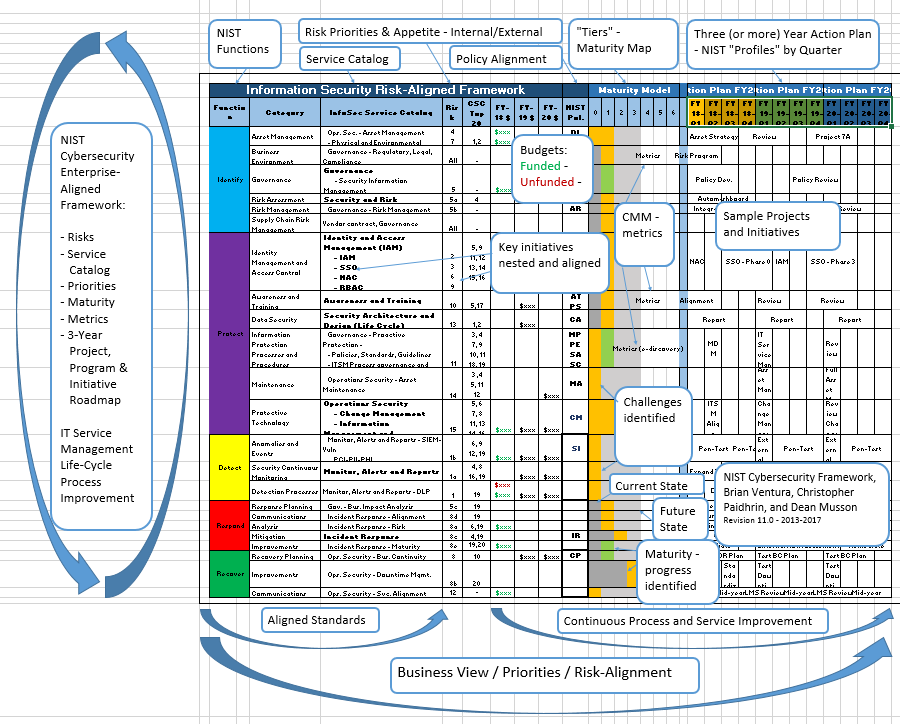
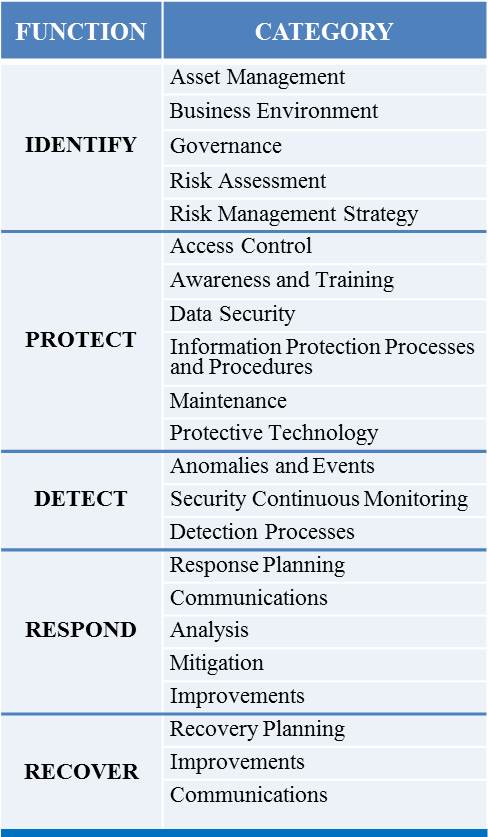
Cyber security implementation plan template. Omb memo m 16 04 cybersecurity strategy and implementation plan csip for the federal civilian government october 30 2015 resulted from a comprehensive review in 2015 of the federal governments cybersecurity policies procedures and practices by the cybersecurity sprint team. The cybersecurity strategy and implementation plan csip and fy2016 cio fisma metrics you are viewing this page in an unauthorized frame window. Now that youve done your research and consulted with your companys team leaders its time to set more explicit goals for your organization. This cyber security strategic plan outlines the goals and objectives of the doe cyber security program to safeguard the does information assets and assure the confidentiality integrity and availability of the information vital to achieve the does missions.
The cyber security program will enhance the defense in depth nature of the protection of cdas associated with target sets. The details of how the department will share information counter new and. The templates and checklists are the various forms needed to create an rmf package and artifacts that support the completion of the emass registration. The information assurance and cyber security strategic plan referred to as the plan has been prepared in response to the chief information officer council cioc enterprise leadership council elc and the enterprise architecture advisory working group ea awg as a vital component.
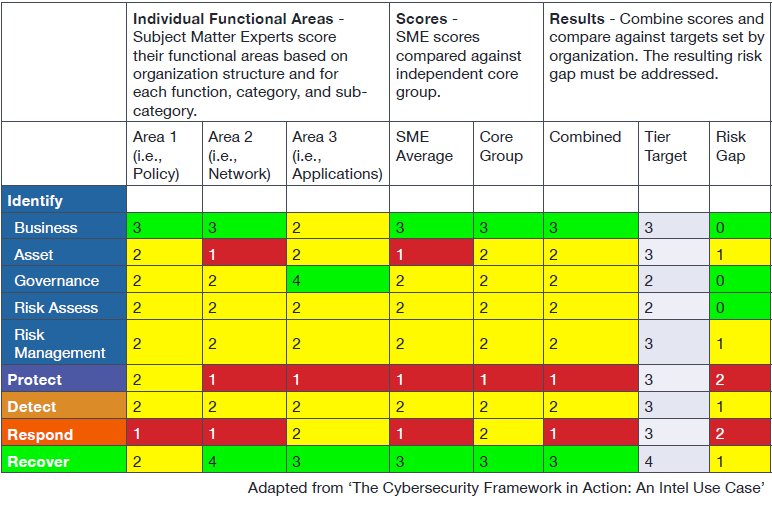
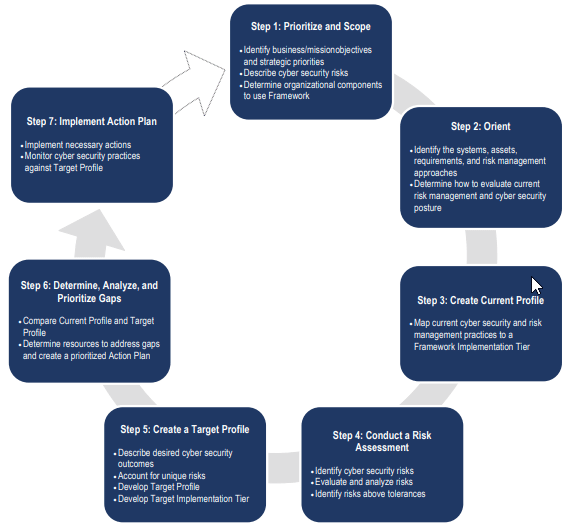
In addition to the templates and checklists refer to the cyber commissioning and the resources and tools pages to review and download the unified facility criteria and the unified facility guide specifications. Its intent was to identify and address critical cybersecurity gaps and emerging priorities and make specific recommendations to address those gaps and priorities. Formal assessment of security controls implementation based on cybersecurity threat and likelihood of exploitation derives the level of residual risk to an information system and data. This document has now been archived and the guidance should not be followed.
Template for cyber security plan implementation schedule from physical harm by an adversary. Cyber implementation plan template contract title mod contract number csm risk reference csm risk level name of supplier current level of supplier compliance reasons unable to achieve full compliance measures planned to achieve compliance mitigate the risk. This is a potential security issue you are being redirected to httpscsrcnistgov. Selection application and maintenance of appropriate security controls.
These goals should be specific to the needs and potential hazards your organization could face. This discovery includes a formal authorization process to. Get the latest from cso by signing up for our newsletters.