Data Breach Risk Assessment Template

Gdpr risk assessment template.
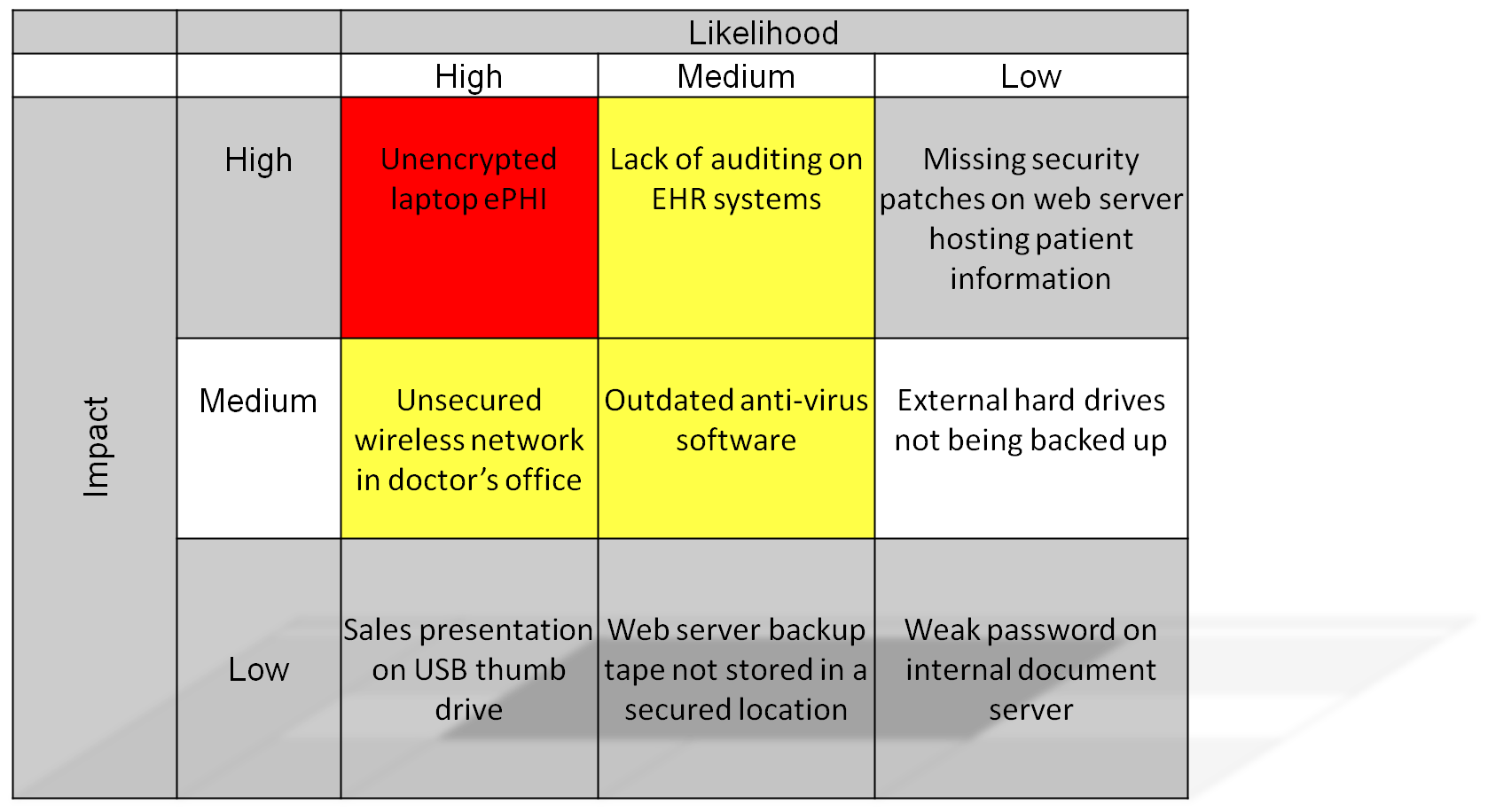
Data breach risk assessment template. Process personal data that could result in a risk of physical harm in the event of a security breach. Surrounding the breach may impact the risk level ranking associate with the data breached. Goal and purpose of the risk based approach prioritising compliance while maximising both privacy and effective use of data. Performing a breach risk assessment retired.
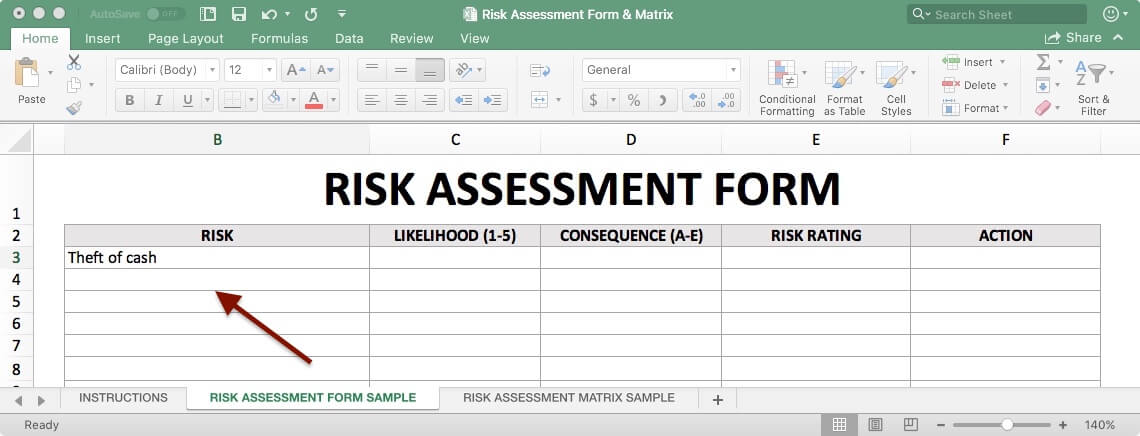
Can the risk of unauthorized access be mitigated by de identifying the pi in whole or part. Can each data element be linked to a valid business or legal reason for collection and use. Is there a risk of further data breaches due to systems being comprised. Data breach assessment guidelines.
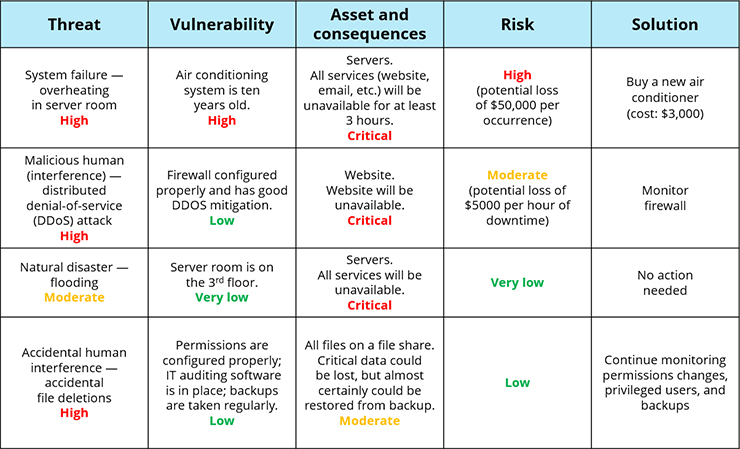
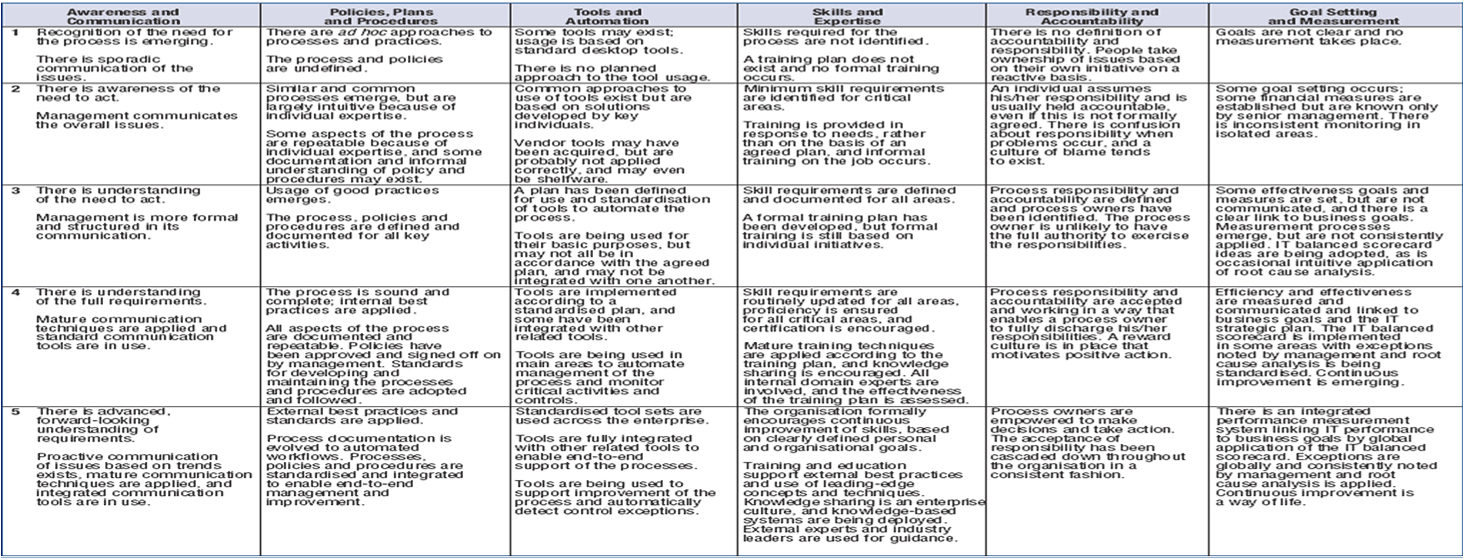
Gdpr requirements including data security security breach notifications privacy by design legitimate interest purpose limitation and fair processing. Home data breach assessment guidelines. However it is not defined on what constitutes risk assessment and what is the definition of risk. Data breach procedure10docx page 5 of 9 d identify and implement any steps to recover any losses and limit the required damage of the breach e if appropriate inform the policeinsurance office 422 assessment of risk all data security breaches must be managed according to their risk.
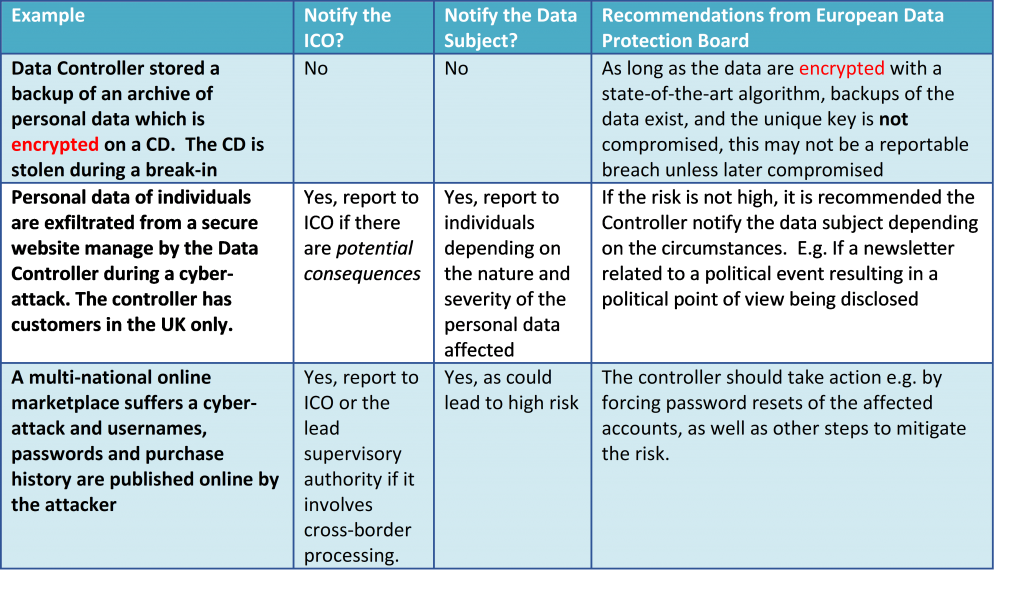
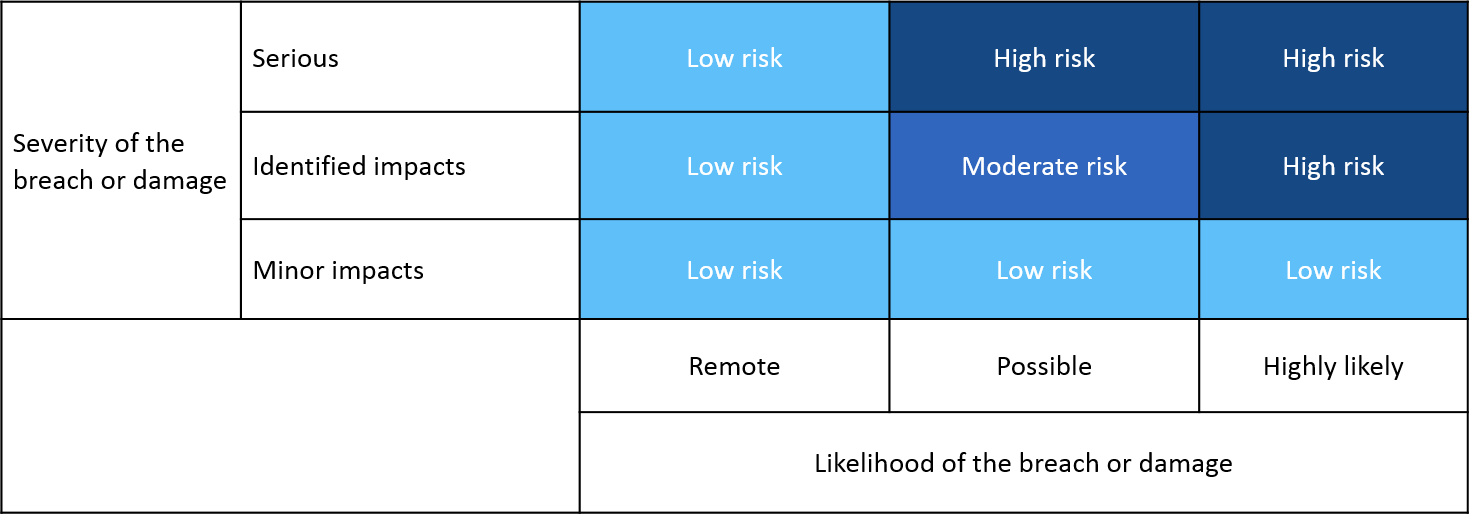
A data protection impact assessment dpia is a process to help you identify and minimise the data protection risks of a project. Low risk dependent on nature of information accessed and cause of breach. High risk dependent on nature of information accessed and cause of breach. Please describe the flow of.
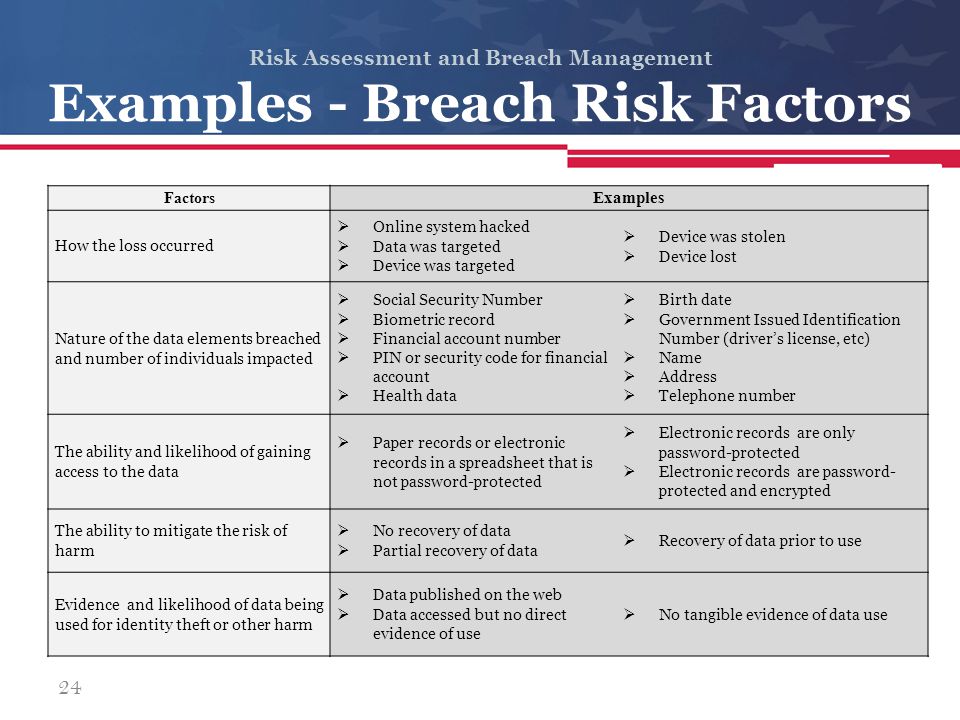
Risk assessment helps organisations to classify. For example if a file of known abuse victims is breached and it includes the victims addresses then you will likely rank the breach of such data as a high probability of risk and potential harm to the persons impacted by the breach. On august 24 2009 the us department of health and human services hhs published 45 cfr parts 160 and 164 breach notification for unsecured protected health information. And document any addition data elements here that may be considered sensitive in the countrys of concern.
The risk assessment is a mandatory portion of every gdpr process. This is because the gdpr applies to a wide variety of the organizations which has data and may be big or small.