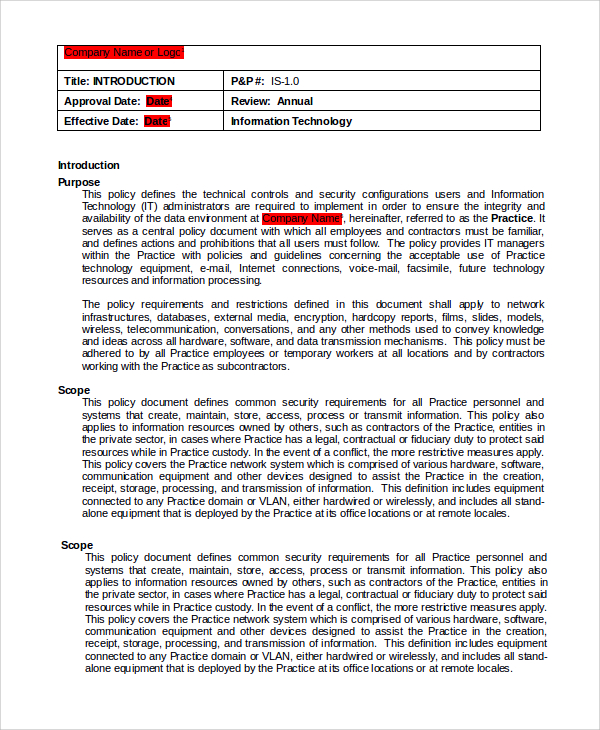
Encryption Policy Template
The purpose of this policy is to define the acceptable use and management of encryption software and hardware throughout the health service executive hse.
Encryption policy template. The export of encryption technologies or encrypted data may be restricted by regulation. This policy was created by or for the sans institute for the. Further this policy shall serve to prohibit company. Encryption products use one or more cryptographic keys to encrypt and decrypt the data that they protect.
The owners of data protected via encryption services shall explicitly assign responsibility for the encryption key management that should be used to protect this data. Email encryption policy purpose this policy shall serve to set forth the guidelines on the use of encryption to secure proprietary information pi related to the company andor protected health information phi when sending such information via email. Encryption offers a means of protecting data in transit or stored on devices but organizations must follow proven methods and adhere to current standards for it to be effective. They also align business goals and strategies with appropriate methods for technically or operationally protecting data.
As business owners determine their requirements for. The purpose of this policy is to provide guidance on the use of encryption technologies to protect lep data information resources and other confidential information or pii while stored at rest or transmitted between parties. Information assurance policies are created to set universal standards for organizations to facilitate data protection. This policy is mandatory and by accessing any information technology it resources which are owned or leased by the hse users are agreeing to abide by the terms of this policy.
Encryption algorithms will not be used. There is no prior approval required. Sample policy on the use of cryptographic controls. This policy also provides direction to ensure that regulations are followed.
All or parts of this policy can be freely used for your organization. This policy outlines tested and recommended encryption technologies to help secure your corporate data. Personnel will seek guidance from the legal department of should export of cryptographic technologies or encrypted data be required. Information assurance policy v23 purpose.