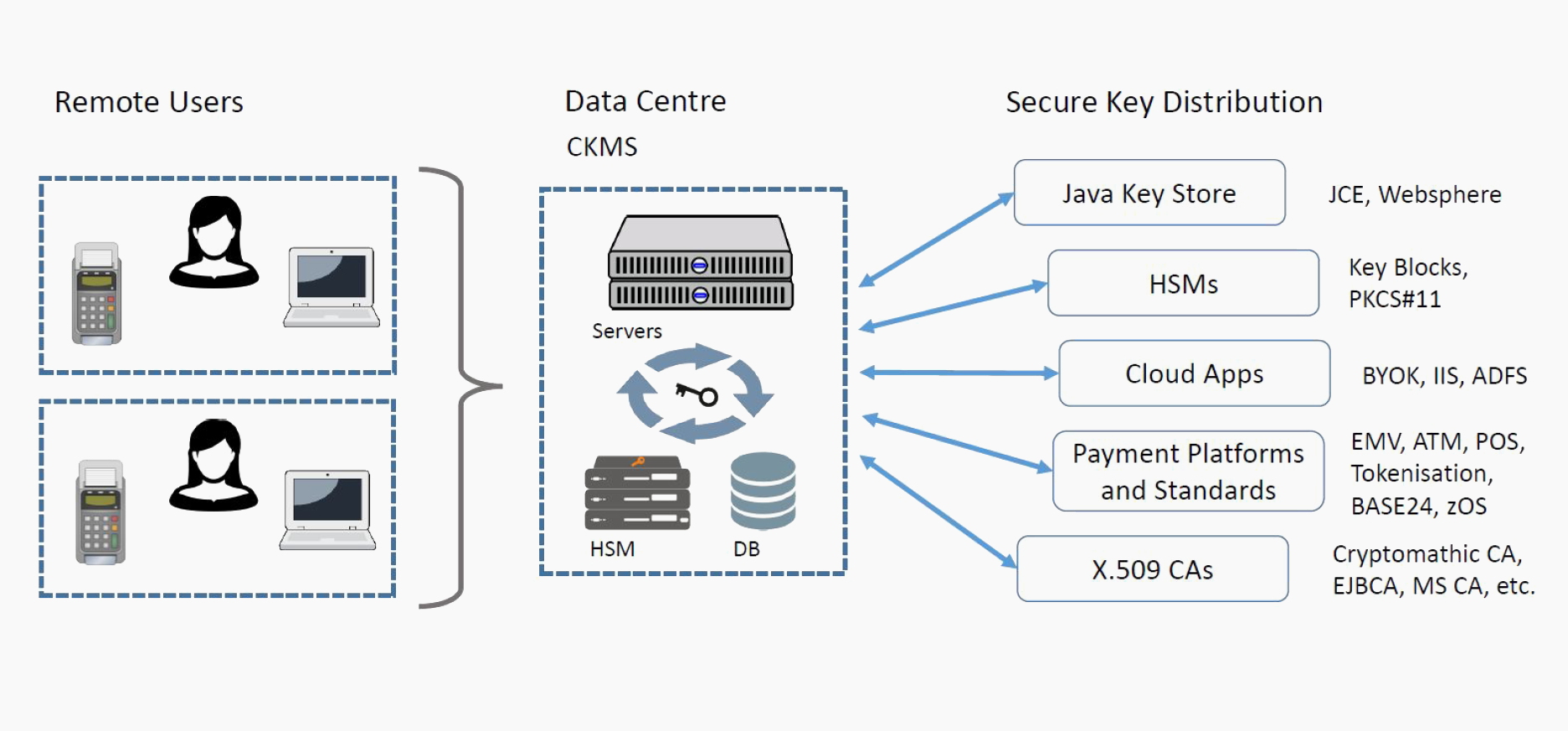
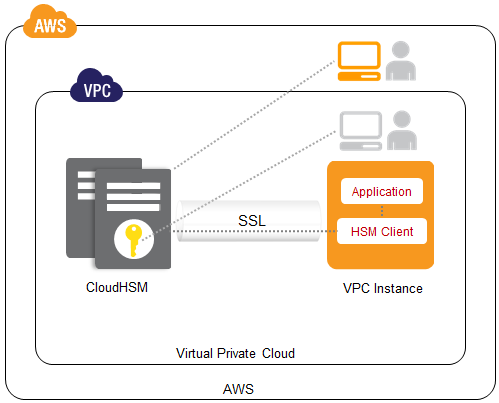
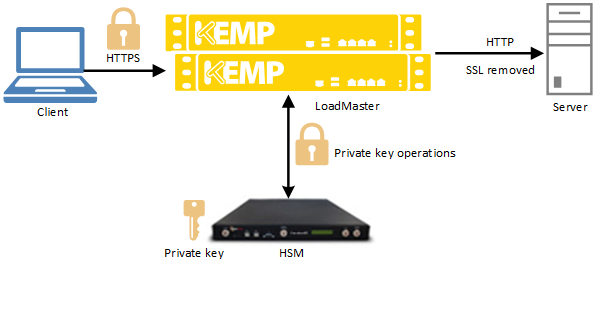
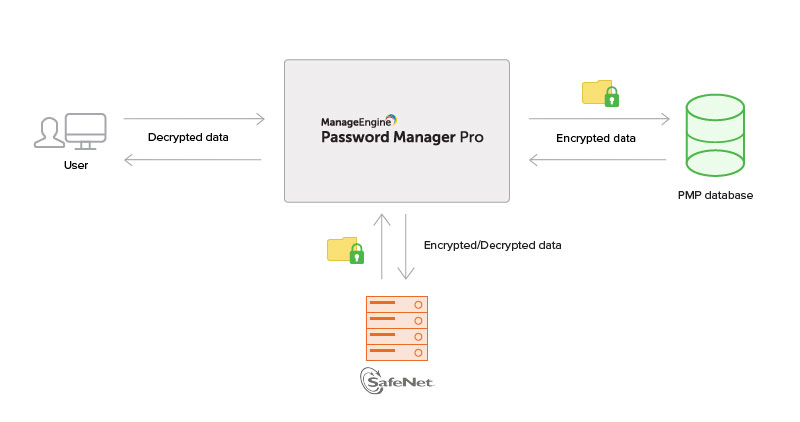
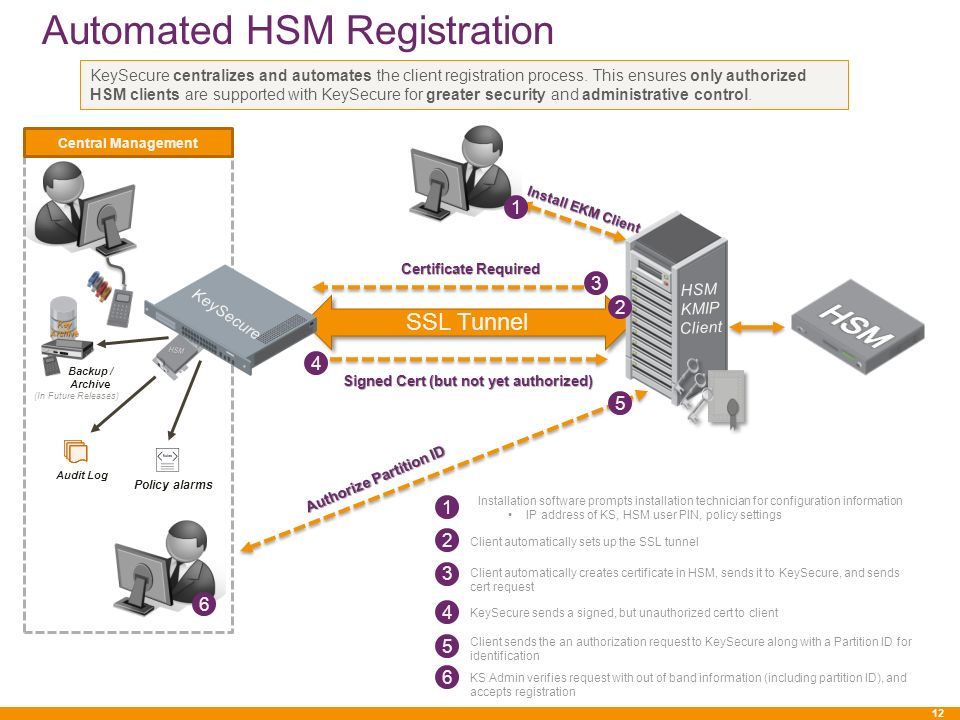
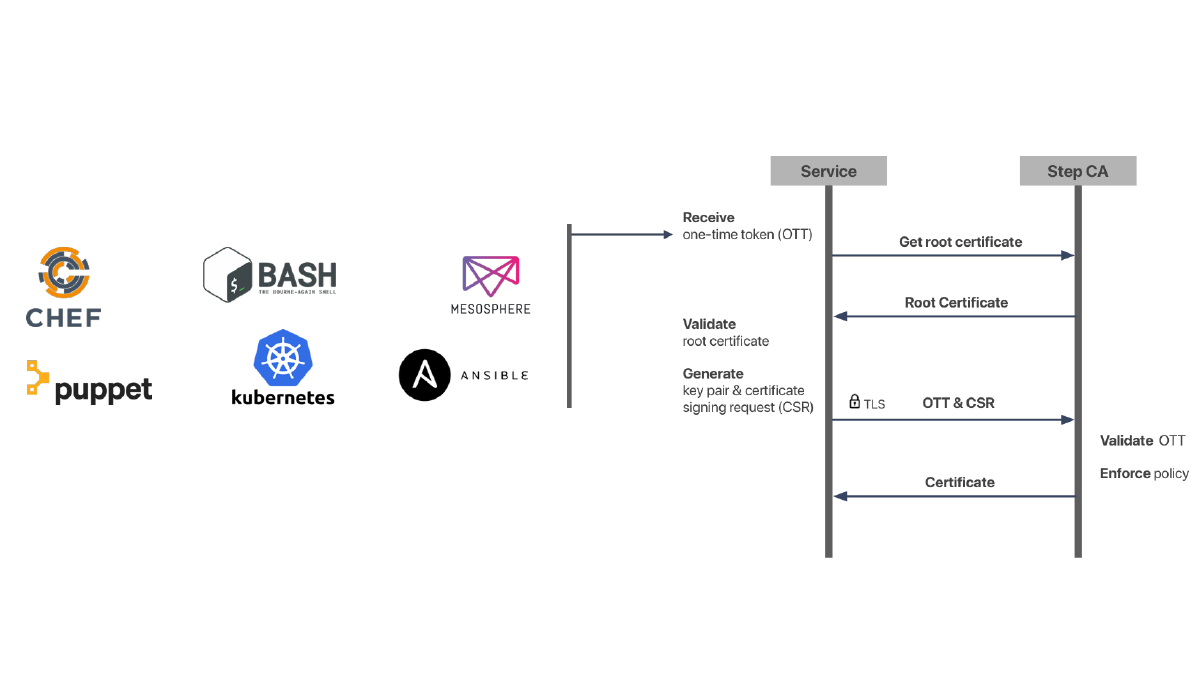
Hsm Certificate Management
It seems to be obvious that cryptographic operations must be performed in a trusted environment.
Hsm certificate management. The hsm certificate program is an outgrowth of the norfolk state university bachelor of science degree in health services management. If youve completed an associate degree from a college listed below you may be eligible to begin mcny as a junior. Transfer students who meet the admissions criteria are also eligible for the 4000 transfer articulation grant. Here is the training class brochure.
Find jobs company reviews. The health services management program is designed to prepare individuals to enter the administrative side of the healthcare field as entry level managers. By meeting that bar the health sector management hsm program. Key management key exchange encryption etc.
A hardware security module hsm is a physical computing device that safeguards and manages digital keys for strong authentication and provides cryptoprocessing. The hsm and hcc experience. Hsm certificate management solution. The most important element of business school for me was a program that would help me gain the knowledge network and experience to succeed in the health care industry long term.
A hardware security module hsm is a dedicated crypto processor that is specifically designed for the protection of the crypto key lifecycle. Skip to job postings search close. Due to over whelming demand for the 4 day pki training course in washington dc i am now forming a class for new york city. I am currently targeting january 2015 and have a limited number of seats remaining.
The hardware security module hsm is a special trusted network computer performing a variety of cryptographic operations. Safenet hardware security modules complement and enhance microsoft active directory certificate services. Contact me for more details. Hardware security modules act as trust anchors that protect the cryptographic infrastructure of some of the most security conscious organizations in the world by securely managing processing and.
These modules traditionally come in the form of a plug in card or an external device that attaches directly to a computer or network server.