Information Security Standards Template

Lots of security professionals think of writing an information security policy as putting pen to paper.
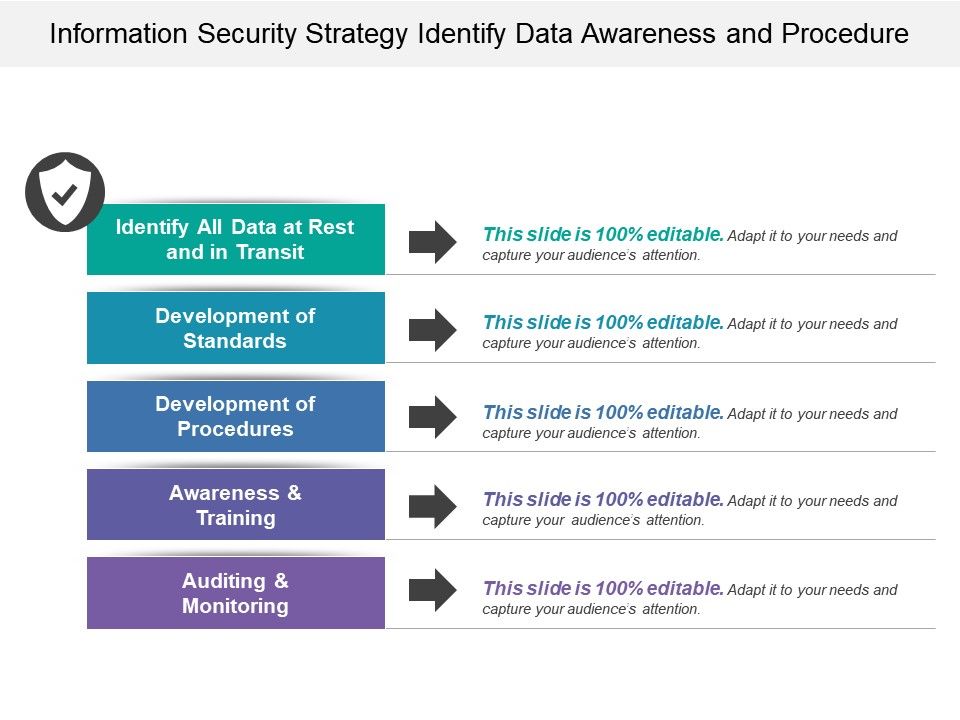
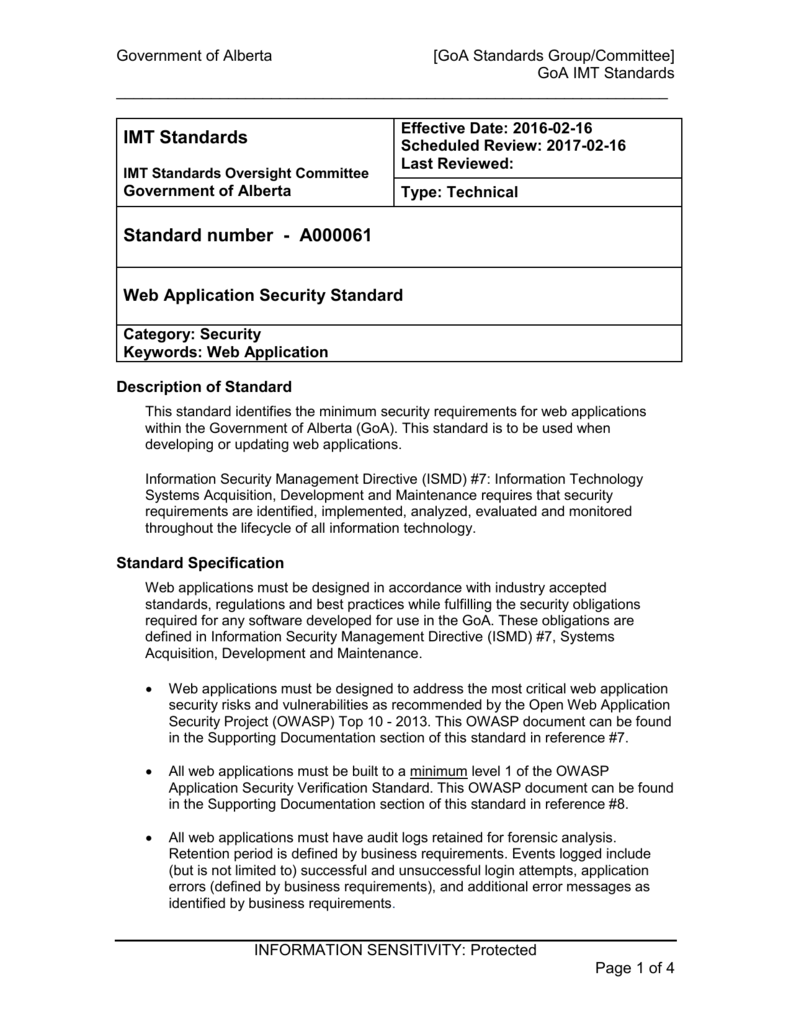
Information security standards template. The ultimate goal of the project is to offer everything you need for rapid development and implementation of information security policies. Information security is governed primarily by cal polys information security program isp and responsible use policy rupthe isp and rup are supplemented by additional policies standards guidelines procedures and forms designed to ensure campus compliance with applicable policies laws and regulations. Refer to the racgp computer and information security standards ciss for explanations of each section to be completed in the templates. Information technology it policies standards and procedures are based on enterprise architecture ea strategies and framework.
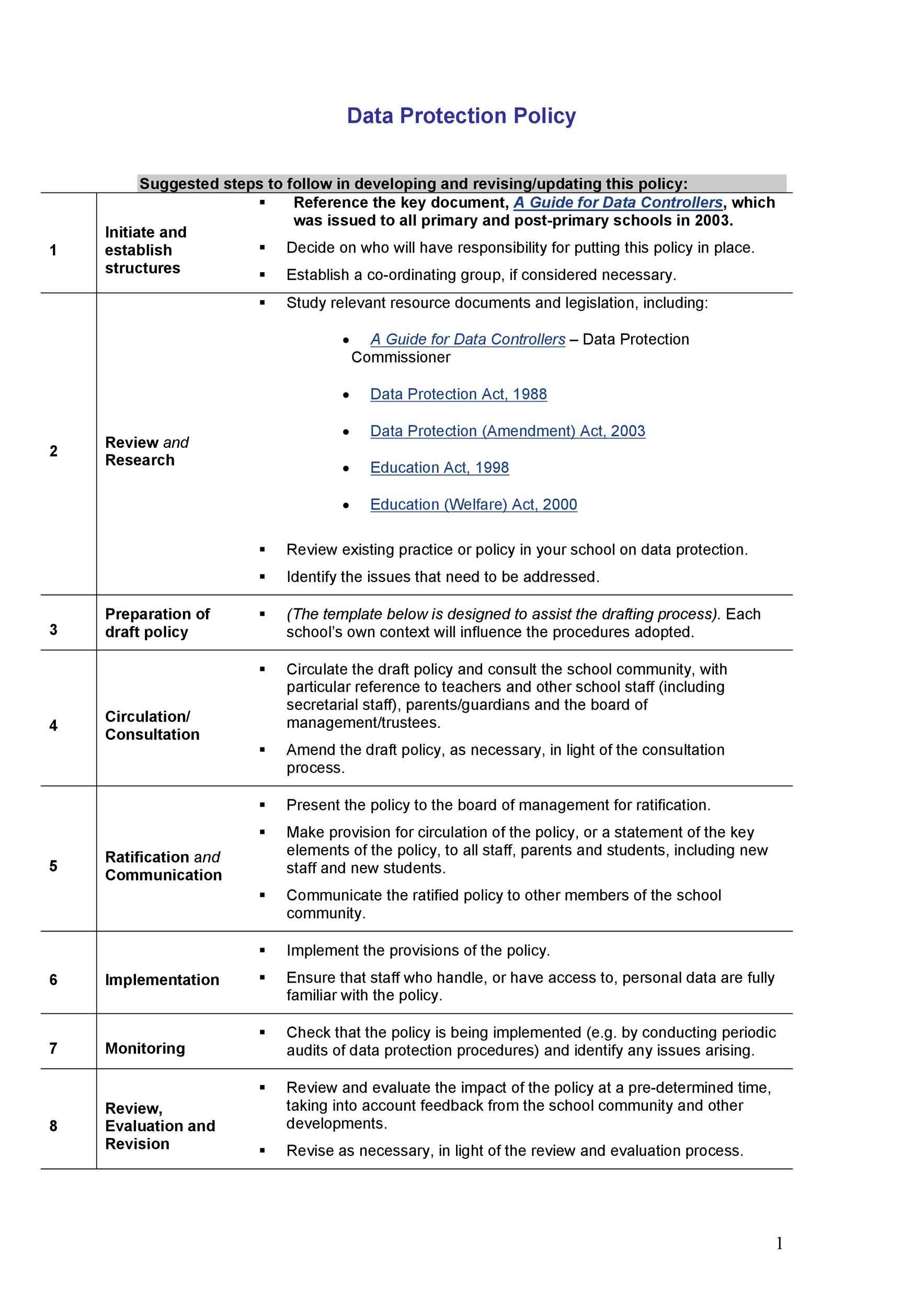
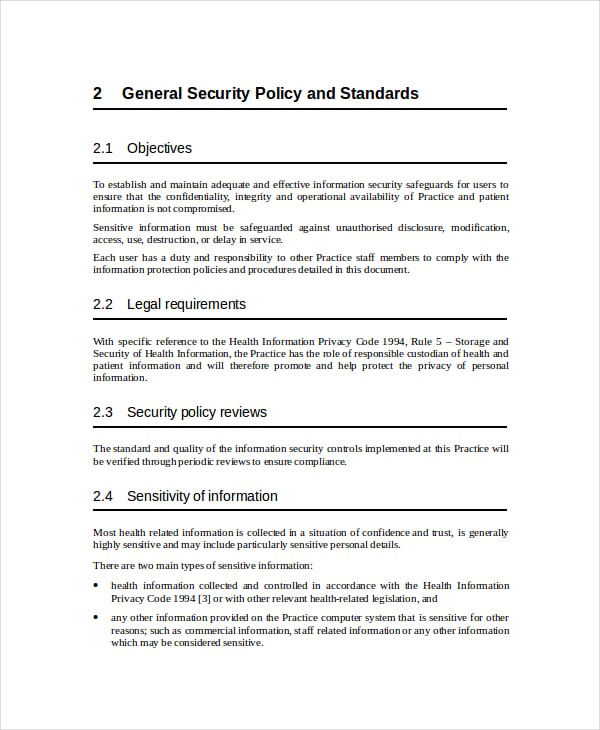
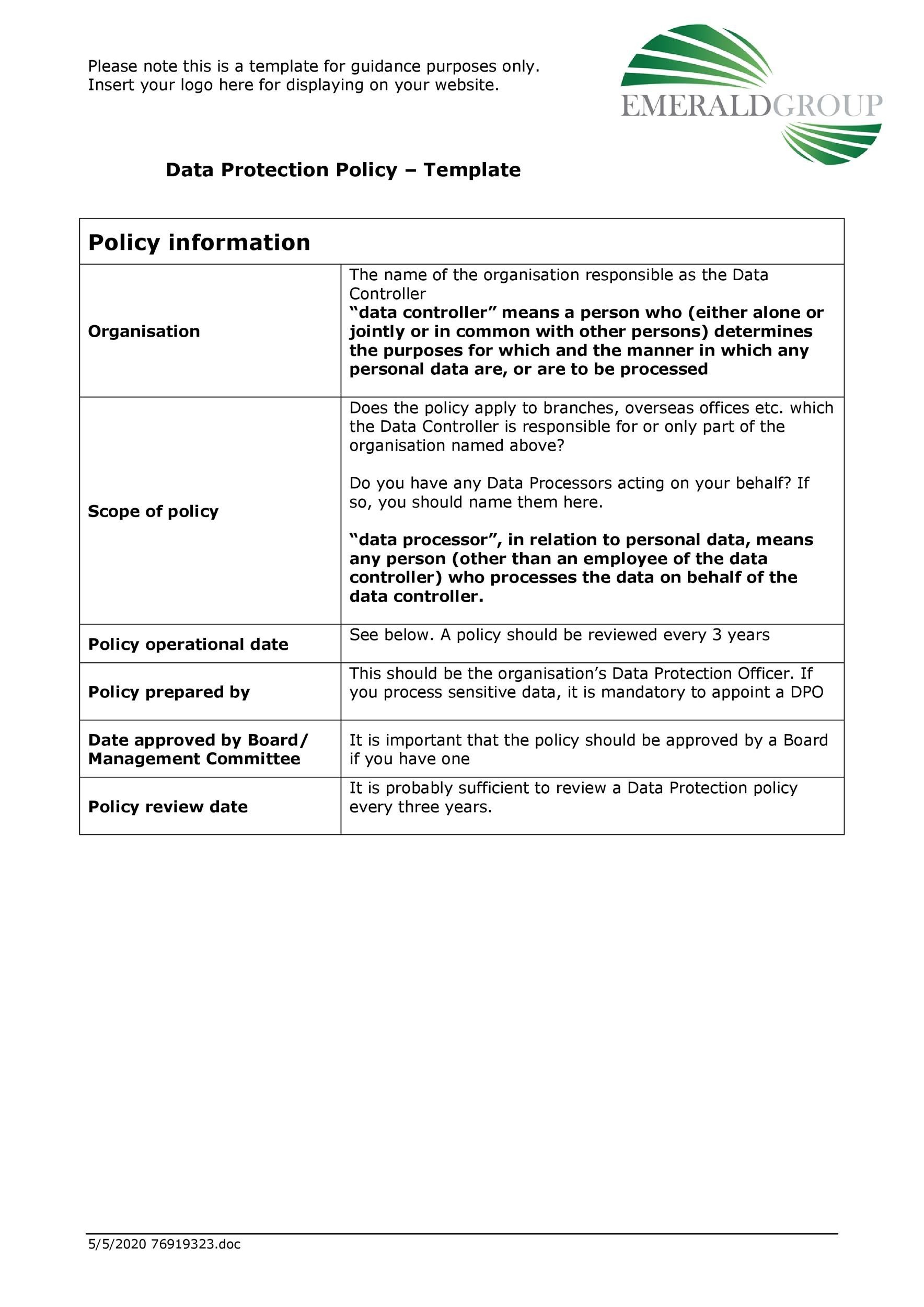
Human resources information security standards final copy v20 page 5 of 11 only have access to the information they need. This document is designed to be completed electronically. Forms checklists and templates. Computer nd information ecuriy tandards fo enera ractice n the ffice base ractices acknowledgements this edition of the royal australian college general practitioners racgp computer and information security standards ciss and the accompanying computer and information security templates have been developed by the racgp.
Sans security policy resource these resources are published by sans institute for the rapid development and implementation of information security policies. The information security standards provide an evolving model for maintaining and improving the information security of the university. Many forms and checklists below are provided as adobe pdf fill in forms and can be filled in and printed from acrobat reader. Guidelines on conducting online businesses and activities.
Ea provides a comprehensive framework of business principles best practices technical standards migration and implementation strategies that direct the design deployment and management of it for the state of arizona. These standards include information security management information security evaluation authentication and authorisation etc. Request that this access be removed as soon as it is no longer required. But really the process starts a lot earlier than that.
These forms may contain javascript. They are based on the security principals of iso the international organization for standardization 27001 27002 and nist national institute of standards and technology. The computer and information security templates when completed will form part of the general practices policies and procedures manual. Find the policy template you need.





:max_bytes(150000):strip_icc()/2060133v1-5bd214c446e0fb00510d020d.png)