Information Security Strategic Plan Template
Check out part two of this series to learn why the ciso should be the central figure responsible for defining an organizations information security strategic plan and aligning it with business.
Information security strategic plan template. Strategic plans covering all aspects of business it and information resource management irm have also been developed and identified as phase ii transformation efforts. What is included in the strategic security plan. The mission statement for a security plan should be outward facing. A seminal and simple to follow template for developing the plan is a strategic planning template for dummies by dr.
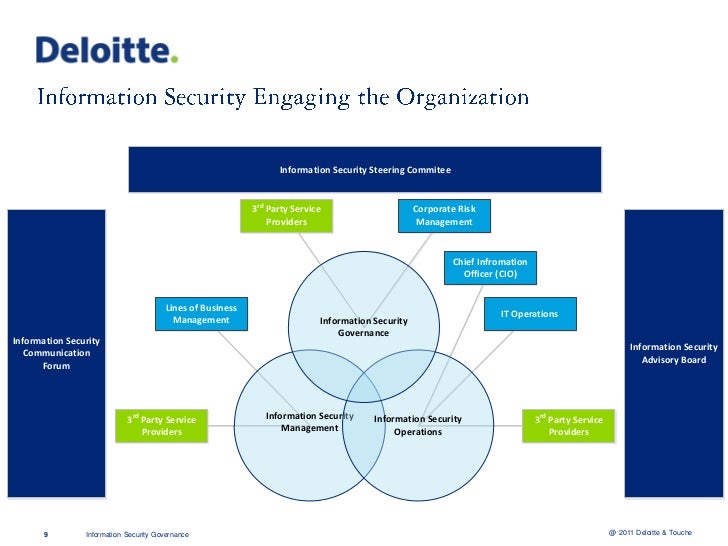
All departments should be on the same page from the very beginning. Build an information security strategy 1. Cyber security strategic plan supporting this initiative. These documents can also deal with the the protection of technologies and systems used by the business the information that are transferred from one business area to another the processes for accepting data and the processes that are involved in normal business operations.
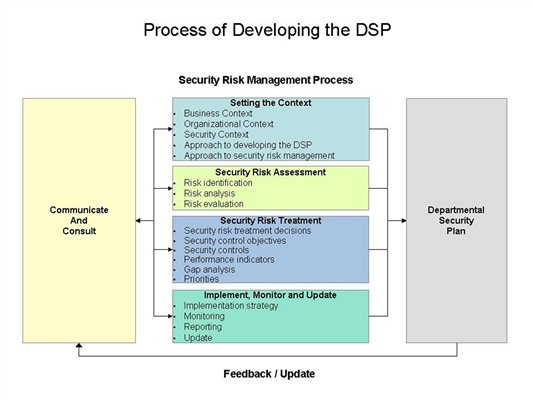
This plan was adapted from the university of colorado systems it security program strategic plan for 2007 2008 the purpose of this sample plan is to establish a formal it security program for your institution. Security strategic plans are not limited for workplace and workforce security. Information classification documents can be included within or as an attachment to the information security plan. Refer to appendix a.
Available resources for a template to complete the information classification activity. Is a global leader in providing it research and advice. The security strategic plan content. Additionally a sample is provided.
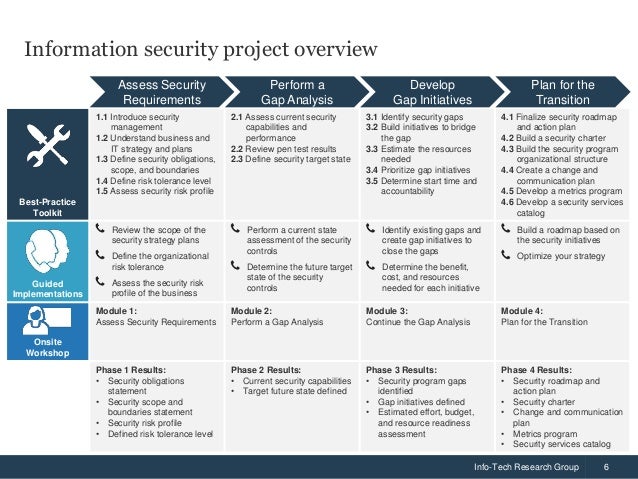
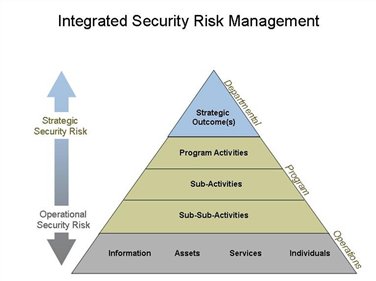
Info tech research group 1info tech research group 1 info tech research group inc. Although the projects and the strategy have been well vetted. Once the ciso has completed this assessment they can begin to develop their strategic plan. To plan this evaluation the ciso will begin with using a risk management framework to assess all collected security information and identify any areas of vulnerability or potential exposure and relating this data to ongoing business activities.