User Access Policy Template

Workforce works remotely on a regular basis.
User access policy template. Before we dive in to look at iso 27001 access control policy examples lets examine the iso 27001 requirement for access control. This article looks at iso 27001 access control policy examples and how these can be implemented at your organisation. Exemplaruser access management policies v11rtf date uncontrolled copy when printed page 7 of 8 10. Free remote access policy template providing remote access is a commonplace business practice with the percentage of people working remotely at an all time high.
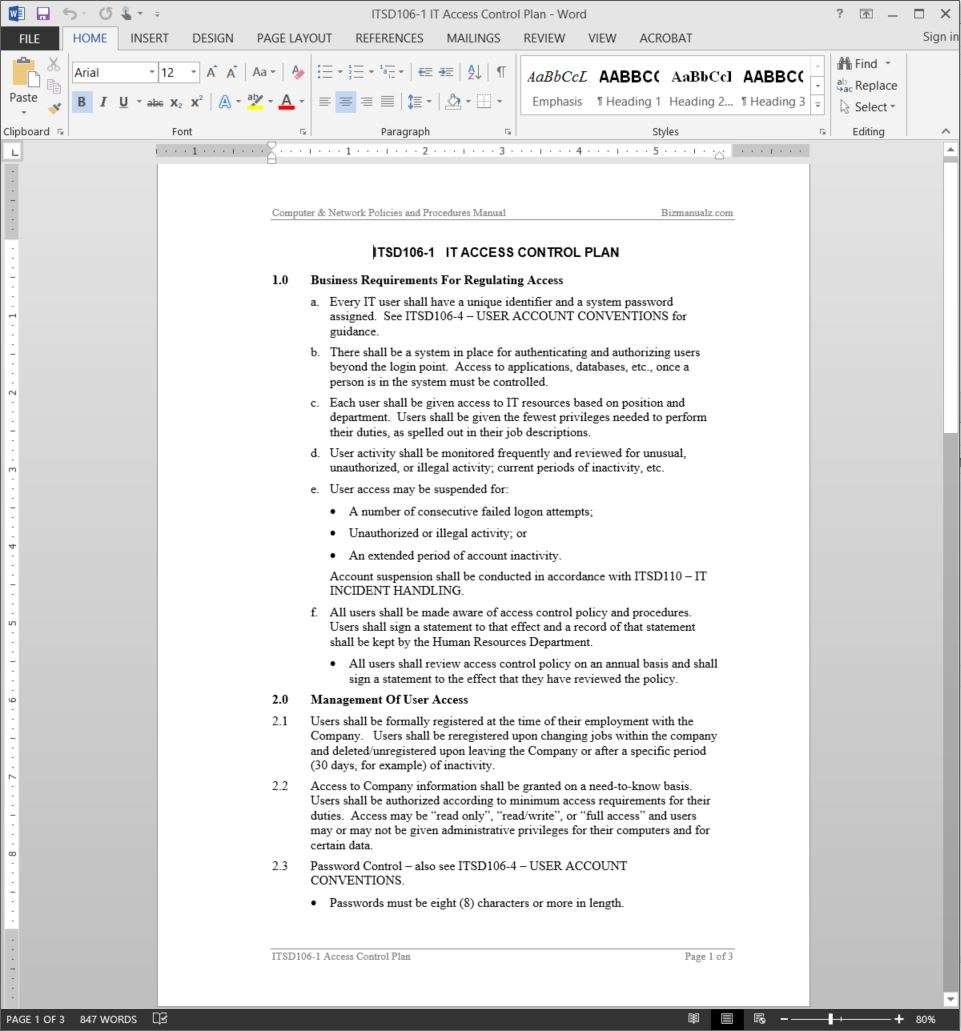
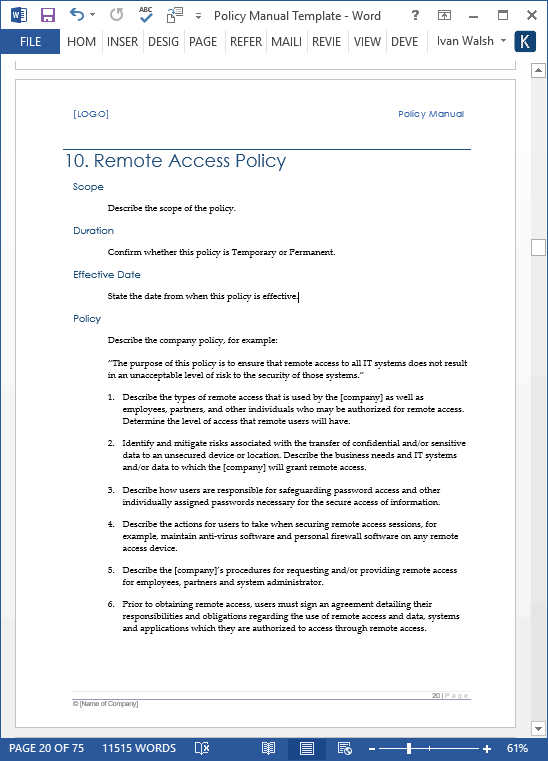
Purpose the purpose of this policy is to maintain an adequate level of security to protect company name data and information systems from. Scope applicability this policy applies to stanford university hipaa components suhc information systems that access use or maintain electronic protected health information ephi and the users requiring access to and administering that data and those systems. Authorized users will not use company name networks to access the internet for outside business interests. Formal user access control procedures must be documented implemented and kept up to date for each application and information system to ensure authorised user access and to prevent unauthorised access.
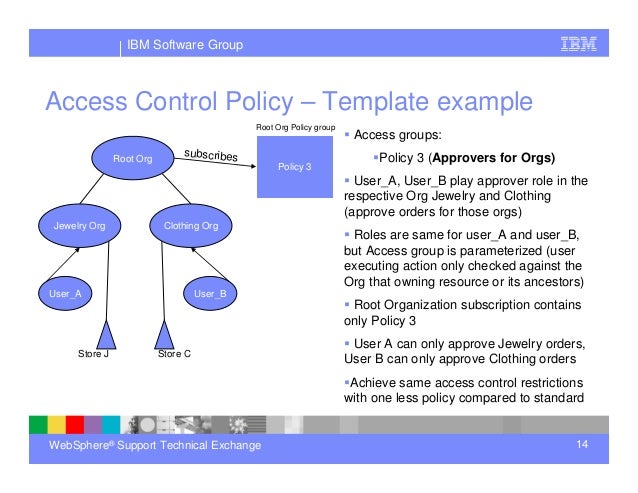
For instance policies may pertain to resource usage within or across organizational units or may be based on need to know competence authority obligation or conflict of interest factors. Review of user access rights the iso will institute a review of all network access rights at least twice a year which is designed to positively confirm all users. Access control is the process that limits and controls access to resources of a computer system. At a high level access control policies are enforced through a mechanism that translates a users access request often in terms of a structure that a.
Applying the policy employee access. Users are students employees consultants contractors agents and authorized users. Our hipaa security policy template policies and procedures templates are ideally suited for following categories of organizations. For further information and definitions see the acceptable use policy.
Used to limit user access to only those network applications and functions for which they have been authorized. Information systems that are managed by or receive technical support from stanford health care shc or. Between 2005 and 2015 the amount of people telecommuting increased by 115 and now nearly a quarter of the us. The authorized user bears responsibility for and consequences of misuse of the authorized users access.