Vulnerability Management Policy Template
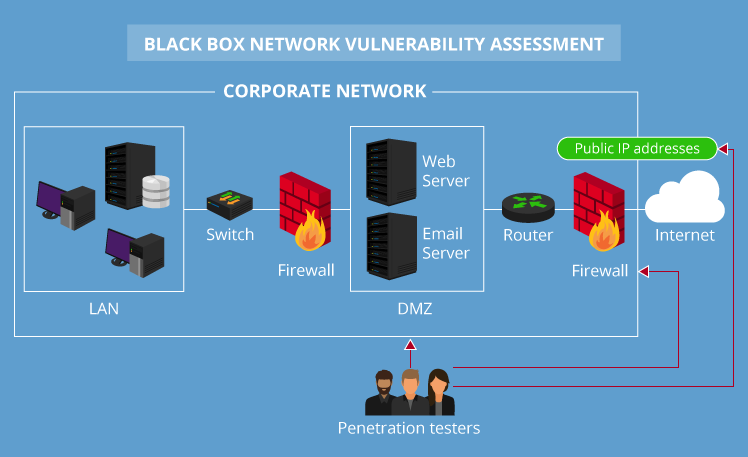
Members of the vulnerability management team.
Vulnerability management policy template. This document details the vulnerability management policies and controls required to maintain high levels of system and application security in a diverse it environment. This is separate from your patch management policy instead this policy accounts for the entire process around managing vulnerabilities. Sample vulnerability management policy. It outlines the technology and.
If you have a. This template will allow you to create a vulnerability management policy. Page1of3 companyname vulnerabilityassessmentpolicy created by or for the sans institute. Information security infosec is charged with helping to protect the universitys electronic information.
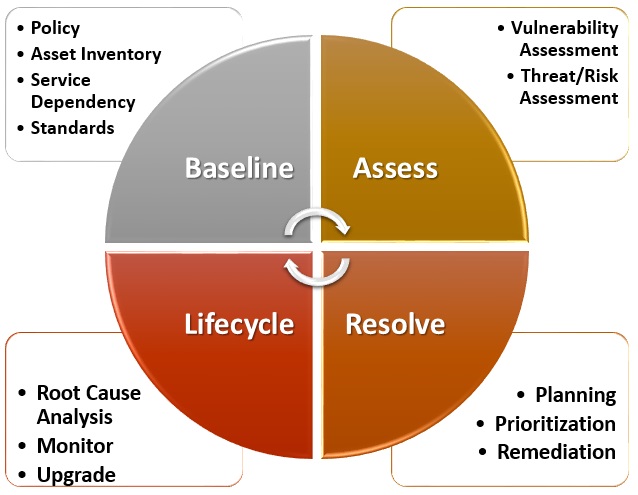
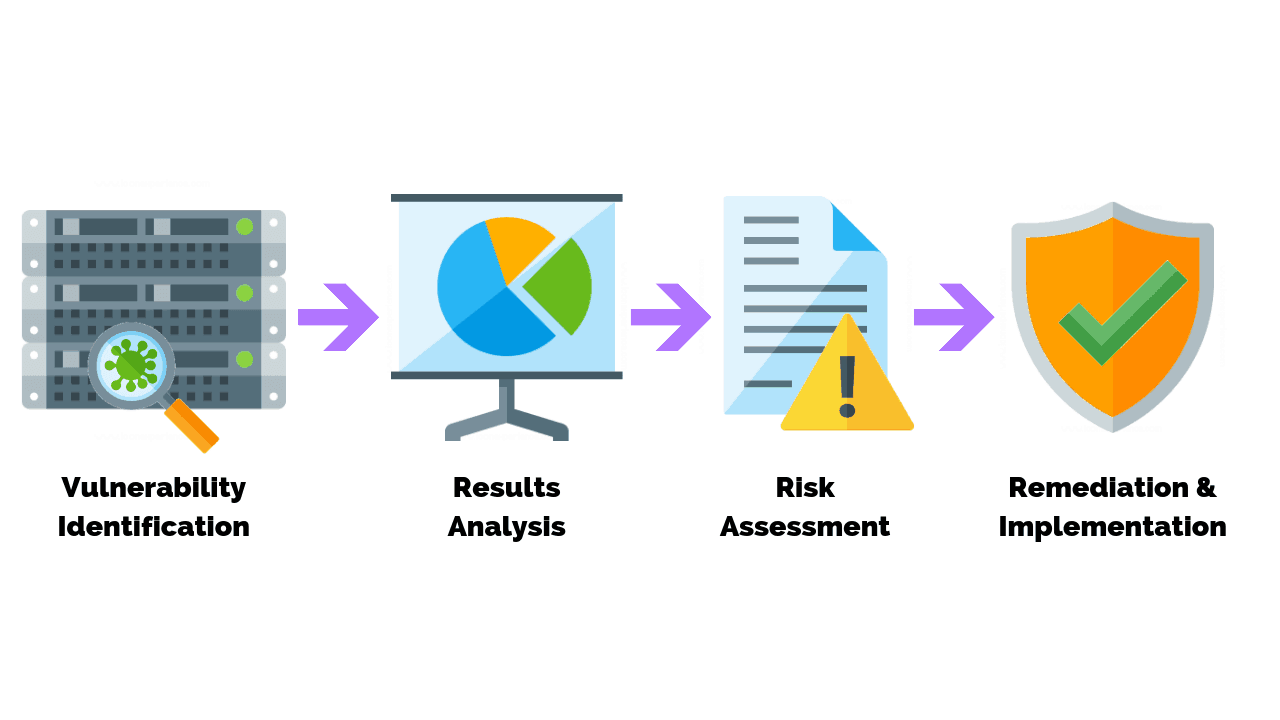
The timely and consistent application of vendor supplied security patches or mitigation of a reported vulnerability are critical components in protecting duke university and duke health network systems and data from damage or loss due to threats such as worms viruses data loss or. The ccc system will create and document systematic and accountable practices to maintain. Vulnerability management policy 50 vulnerability management process and procedures it goes through a continuous cycle of scanning and remediating vulnerabilities through a series of quarterly system and network scans configuration templates and checklists and adhering to best practice when implementing new business solutions. Vulnerability management policy 3 company name introduction and purpose this document details the vulnerability management policies and controls required to maintain high levels of system and application security in a diverse it environment.
Scope of the program. The subsequent vulnerability management program policy and procedures within the below referenced material incorporate all the major provisions as listed above along with other supporting elements for ensuring a comprehensive and in depth document. Vulnerability management extends to other relevant domains within an organization. This information technology policy directs the establishment of vulnerability management practices in order to proactively prevent the exploitation of vulnerabilities and potential loss of ccc sensitive data.
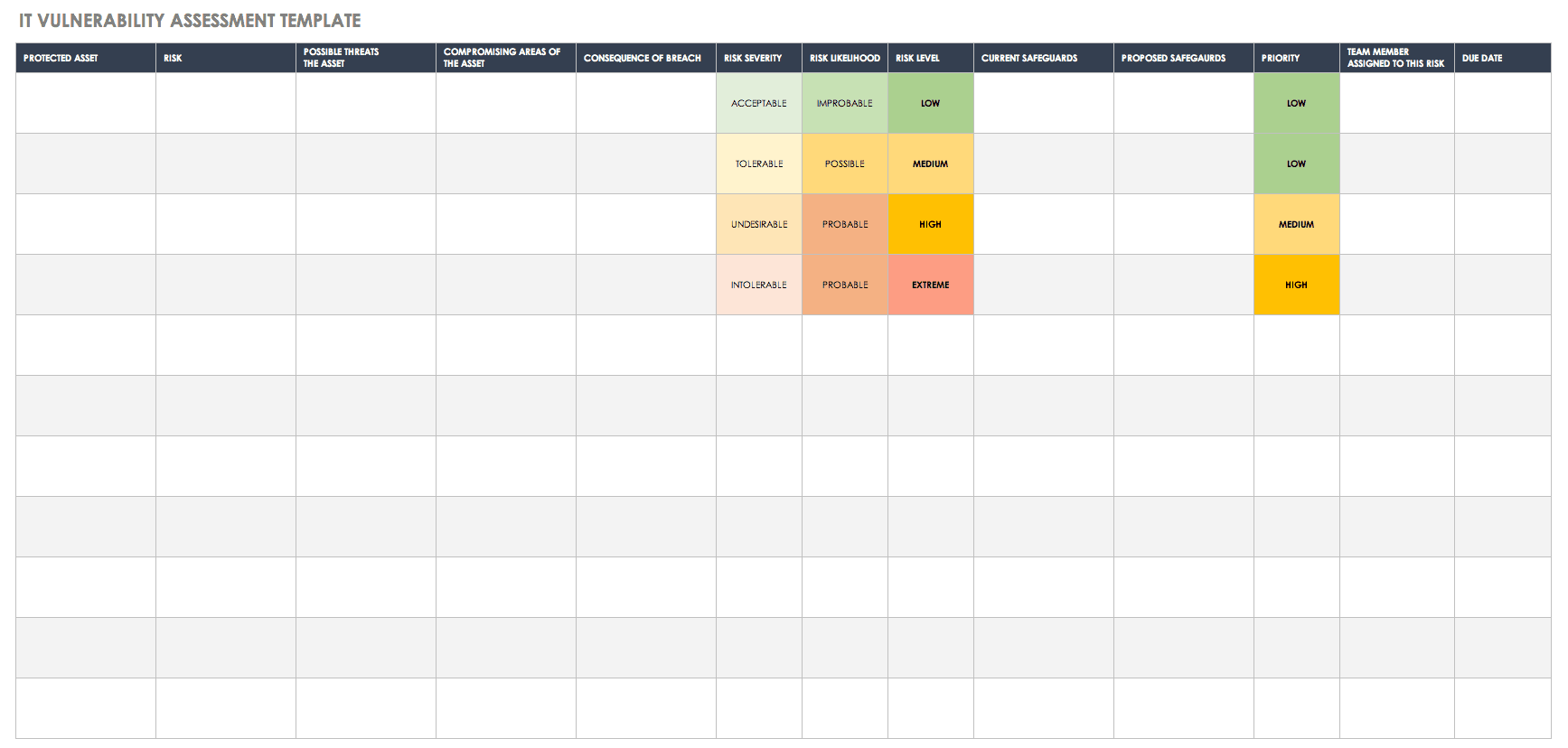
Scanning schedule for vulnerability scanning. It outlines the technology and procedures necessary for implementing a comprehensive integrated program to detect and.