Cryptography Formula And Diagram
Lattice based cryptography is the generic term for constructions of cryptographic primitives that involve lattices either in the construction itself or in the security prooflattice based constructions are currently important candidates for post quantum cryptographyunlike more widely used and known public key schemes such as the rsa diffie hellman or elliptic curve cryptosystems which are.
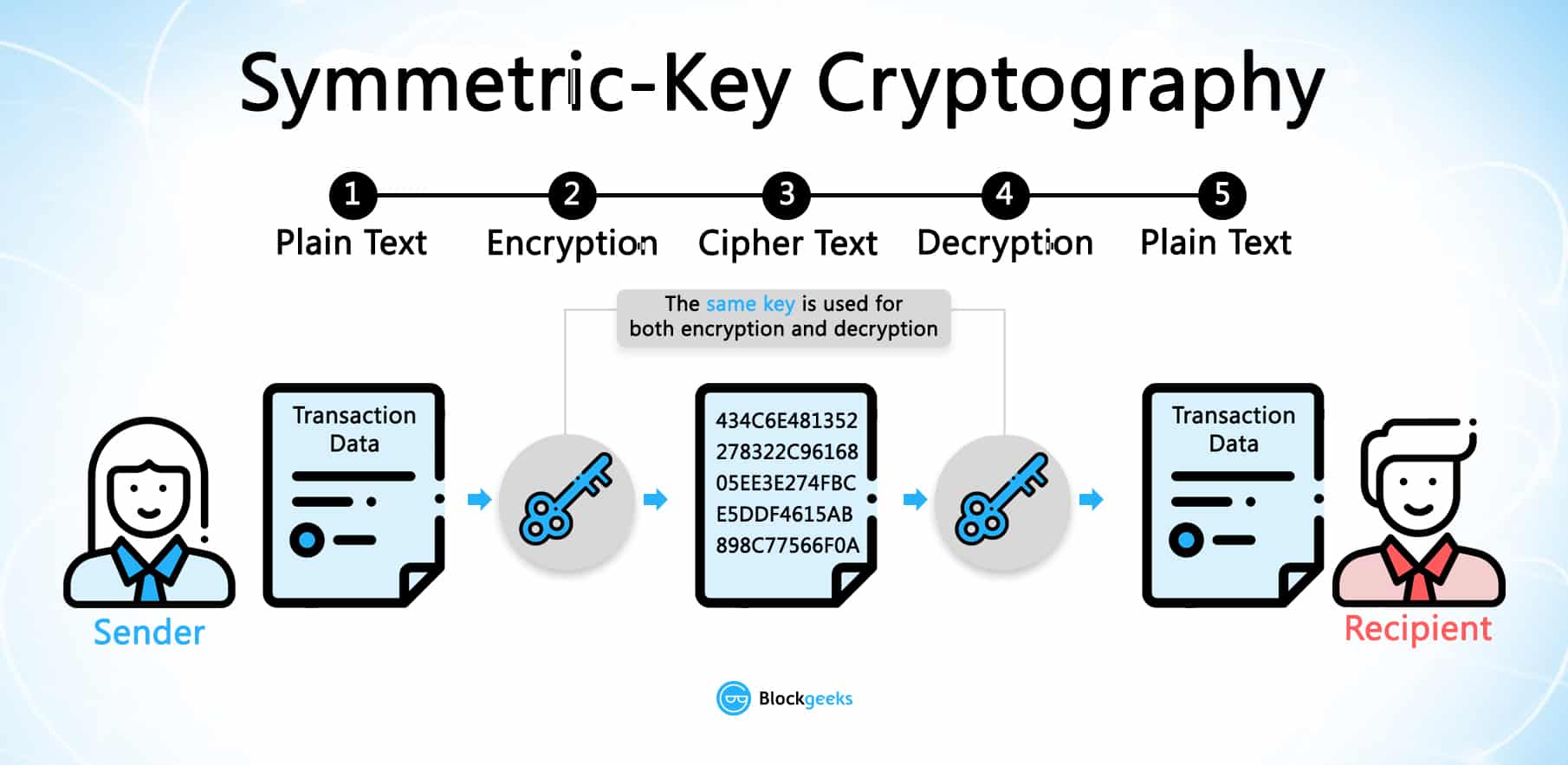
Cryptography formula and diagram. And grafein graphein to write or logia logia study respectively is the practice and study of techniques for secure communication in the presence of third parties called adversaries. It is not recommended however it is possible while working with block ciphers to use the same secret key bits for encrypting the same plaintext parts. Elliptic curve cryptography ecc is an approach to public key cryptography based on the algebraic structure of elliptic curves over finite fields. How many keys are involved for symmetric key encryption.
Early public key systems such as the rsa algorithm are secure assuming that it is difficult to factor a. Only person i and person j can decrypt each others messages. C e k p p d k c where p plaintext c ciphertext e the encryption method d the decryption method and k the key. How about public key encryption.
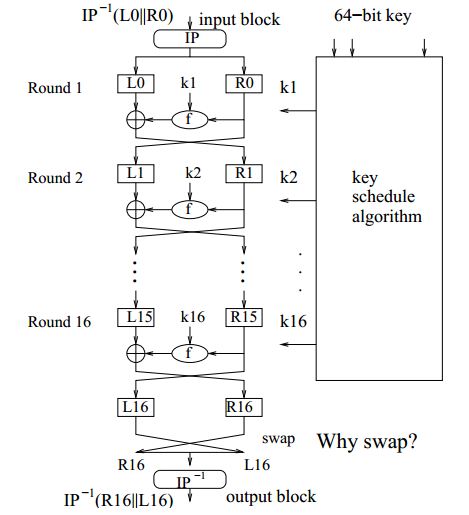
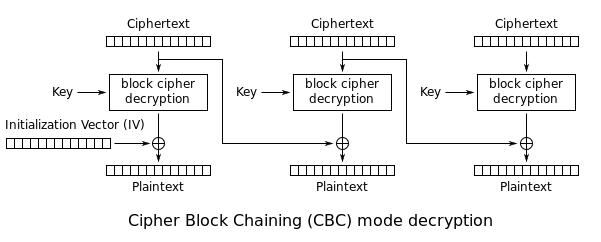
For those who like formulas this process is sometimes written as. 7 public key cryptography 105 71 the theoretical model 105 711 motivation and set up 105. I have a problem where i have to figure this out and it would be great to. In cryptography a block cipher mode of operation is an algorithm that uses a block cipher to provide information security such as confidentiality or authenticity.
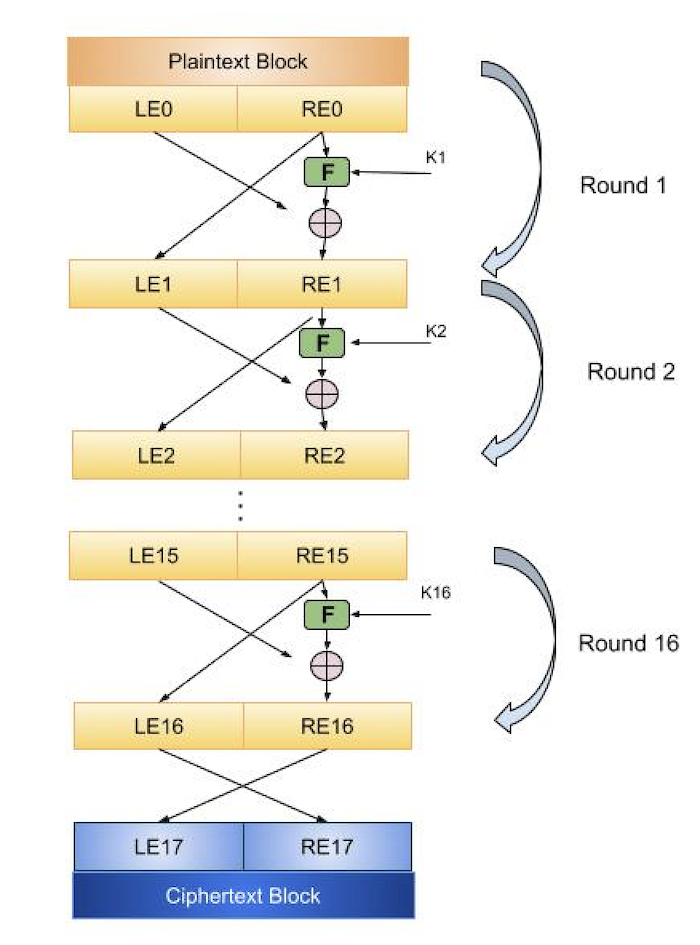
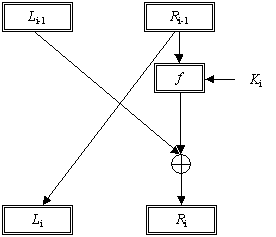
I believe the diagram is correct since two swaps is equivalent to no swaps. The modes of operation of block ciphers are configuration methods that allow those ciphers to work with large data streams without the risk of compromising the provided security. It would be really useful to have an example formula for the keyspace of a feistel and an explanation. Use the mathematica function permutations and the input formula at the end of section 13 to.
Public key cryptography is based on the intractability of certain mathematical problems. This article is within the scope of wikiproject cryptography. 48 fundamentals of cryptology. Cryptography or cryptology from ancient greek.
All communication between any two people i and j is visible to group n. Suppose you have n people who want to communicate with each other using symmetric keys. A block cipher by itself is only suitable for the secure cryptographic transformation encryption or decryption of one fixed length group of bits called a block. More often rsa passes encrypted shared keys for symmetric key cryptography which in turn can perform bulk encryption decryption operations at much higher speed.