Information Security Report Template

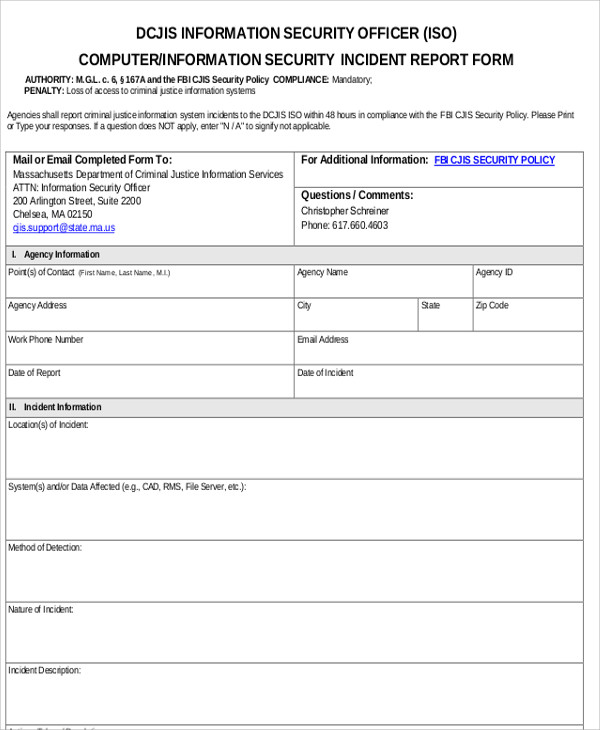
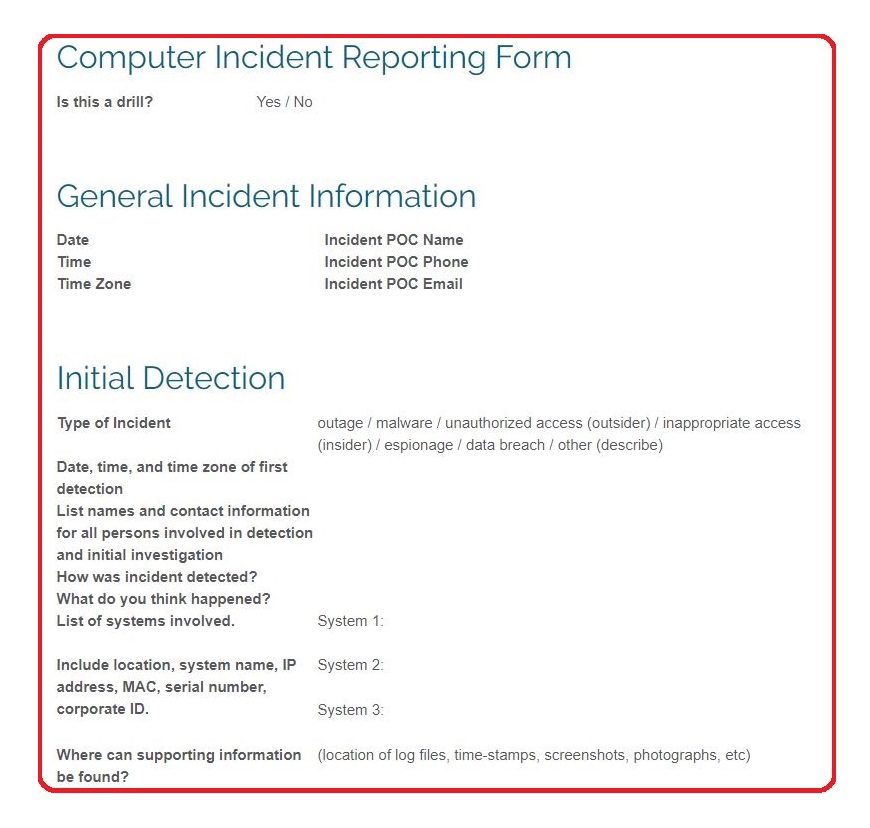
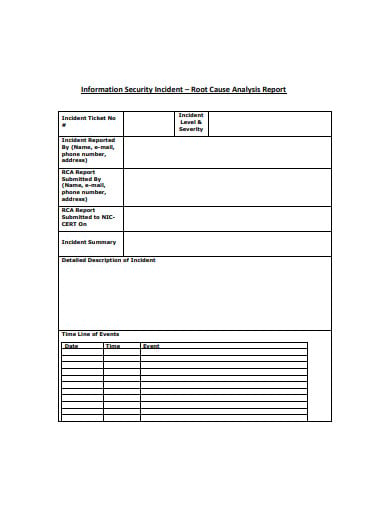
Security incident reports are very important summaries of misdemeanor or criminal incidents that security staff must file not just in accordance to company rules but for police authorities who need a written account of the incident for the filing of an official incident report since incident reports are used for filing of cases and insurance purposes.
Information security report template. Cyber insurance executive summary report client name here cyber risk summary about peer benchmarking. Audit objectives and scope. Detailed risk assessment report executive summary during the period june 1 2004 to june 16 2004 a detailed information security risk assessment was performed on the department of motor vehicles motor vehicle registration online system mvros. O generate current network diagrams.
This will likely help you identify specific security gaps that may not have been obvious to you. The call to action. Security assessment report template docx home. It should include or refer to the following.
Cms hhs websites cms global footer. 7500 security boulevard baltimore md 21244. A federal government website managed and paid for by the us. Finally wrap up the presentation with a closing slide to reiterate the main points and any action items.
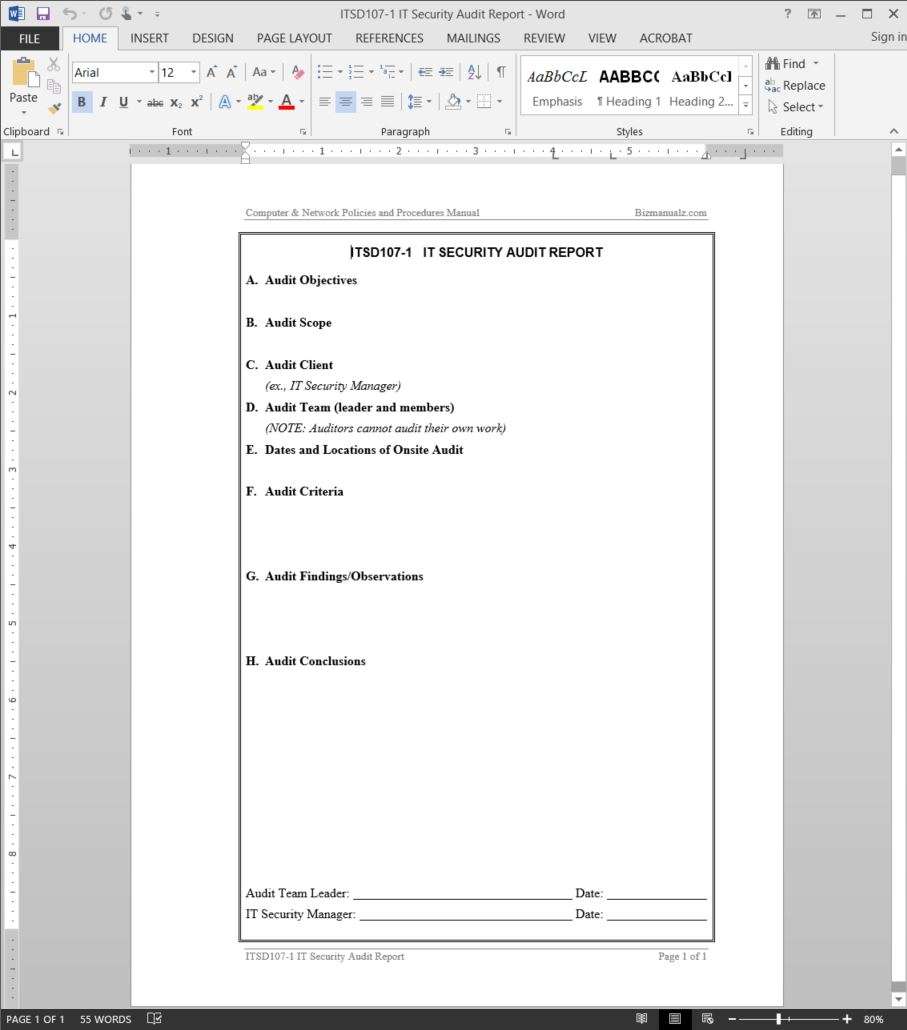
A cyber security risk assessment report will guide you in articulating your discoveries during your assessment by asking questions that prompt quality answers from you. The it security audit report template should provide a complete accurate clear and concise record of the audit. Centers for medicare medicaid services. Template for security assessment report.
The mvros provides the ability for state vehicle owners to renew motor vehicle. This report includes information about how client name compares to its peers with respect to its cyber risk landscape including threat likelihood business impact in the event of a cyber incident and control strength. Cyber security and risk assessment template. Itsd107 1 it security audit report should be prepared approved and distributed by the audit team.
Slides 3 through 6 should discuss how external events will affect security an assessment of the existing risk position this can change depending on acquisitions and other events and the entire security strategy. O formalize information security documentation to progress from an ad hoc state to a more mature structured state for managing it and information security. O enable logging on all information systems and network devices.